Corporate Espionage: Office365 Hack Nets Millions For Cybercriminal
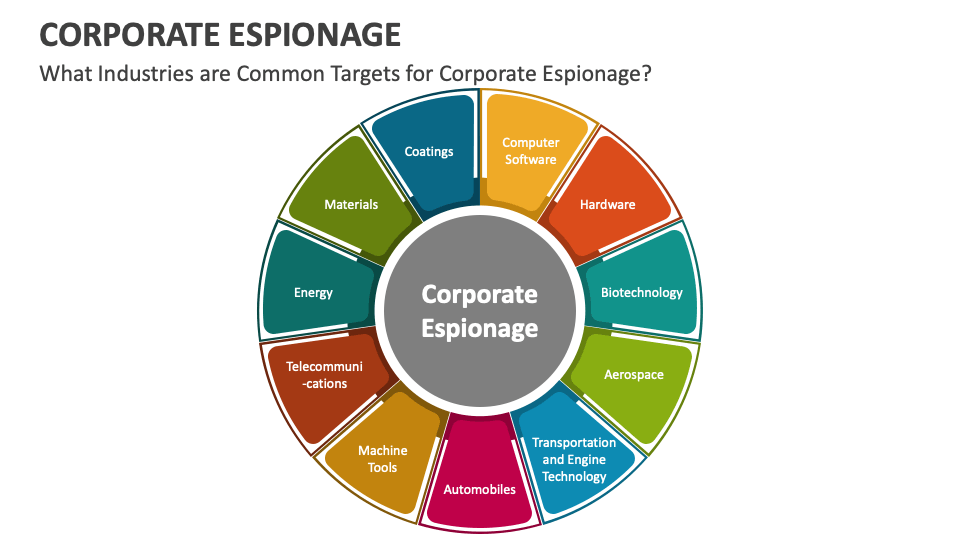
Table of Contents
The Anatomy of the Office365 Hack
This specific Office365 hack exploited several common vulnerabilities, demonstrating the multifaceted nature of modern cybercrime. The attackers employed a combination of techniques, highlighting the sophistication of these attacks and the need for multi-layered security.
The attack likely unfolded in several stages:
-
Initial Access: The hackers likely gained initial access through a spear-phishing campaign. These targeted emails, designed to look legitimate, often contain malicious attachments or links that, when clicked, install malware on the victim's computer. Alternatively, credential stuffing, using stolen usernames and passwords from other breaches, may have been employed. Zero-day exploits, targeting previously unknown vulnerabilities, are also a possibility.
-
Lateral Movement: Once inside the network, the attackers used various techniques to move laterally, gaining access to other systems and accounts. This could involve exploiting weak passwords, compromised accounts with elevated privileges, or leveraging vulnerabilities in third-party applications.
-
Data Exfiltration: After gaining access to sensitive data, the attackers exfiltrated it using various methods, including compromised accounts, cloud storage services, and covert communication channels. They likely used encryption and anonymization techniques to conceal their actions and hinder investigation.
-
Covering Tracks: Finally, the attackers attempted to cover their tracks, deleting logs, modifying system settings, and employing other methods to prevent detection.
The stages of the attack might look like this:
- Spear phishing email targeting high-level employees with access to sensitive data.
- Exploitation of weak passwords or compromised accounts with administrative privileges.
- Access to sensitive data stored in SharePoint, OneDrive, or Exchange Online.
- Use of file synchronization services for data exfiltration.
- Implementation of encryption and anonymization techniques to obscure their activity.
- Deletion of logs and modification of system configurations to cover their tracks.
Statistics reveal alarming success rates for such attacks. According to [insert reputable source and statistic on successful Office365 phishing attacks], a significant percentage of phishing emails successfully compromise accounts. The average cost of data breaches, as reported by [insert reputable source and statistic on average cost of data breaches], runs into millions of dollars, impacting even the largest organizations.
The Stolen Data and its Impact
The data stolen in this Office365 hack likely included a mix of sensitive information, depending on the targeted accounts and departments. This could encompass:
- Financial records, including bank account details, transaction history, and financial projections.
- Intellectual property, such as patents, designs, trade secrets, and research data.
- Customer data, containing personal information, contact details, and purchase history.
- Strategic plans, including business strategies, marketing plans, and expansion projects.
The consequences for the victim company are severe and far-reaching:
- Financial Losses: Millions in revenue could be lost due to intellectual property theft, compromised financial data, or disruption of business operations.
- Reputational Damage: Data breaches severely damage brand reputation, leading to loss of customer trust and potential boycotts.
- Legal Repercussions: Companies face significant fines and legal settlements due to regulatory non-compliance and potential lawsuits from affected customers.
- Competitive Disadvantage: The theft of strategic plans and intellectual property can provide competitors with a significant advantage, impacting market share and profitability.
Preventing Office365 Corporate Espionage
Protecting your organization from Office365 corporate espionage requires a multi-layered security approach. The following measures are crucial:
- Multi-Factor Authentication (MFA): Implement MFA for all Office365 accounts to add an extra layer of security, even if passwords are compromised.
- Strong Password Policies: Enforce strong password policies and encourage the use of password management tools to prevent credential stuffing and brute-force attacks.
- Employee Security Awareness Training: Regularly train employees on phishing recognition, safe browsing practices, and password hygiene to reduce the risk of social engineering attacks.
- Advanced Threat Protection: Utilize advanced threat protection features within Office365 to detect and block malicious emails, attachments, and links.
- Data Loss Prevention (DLP): Implement DLP policies to monitor and prevent sensitive data from leaving the organization's control.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and ensure that security measures are effective.
- Access Control and Permissions: Regularly review and audit access privileges and user permissions to ensure that only authorized personnel have access to sensitive data.
The Role of Third-Party Applications
Third-party applications integrated with Office365 pose a significant risk. Compromised third-party apps can provide attackers with a backdoor into your organization’s data. Thoroughly vet third-party vendors, carefully review application permissions, and regularly review and revoke access to applications no longer needed.
Conclusion: Protecting Your Business from Office365 Corporate Espionage
The vulnerability of Office365 to corporate espionage is clear. The devastating consequences – financial losses, reputational damage, and legal repercussions – underscore the urgent need for proactive security measures. Don't become the next victim of Office365 corporate espionage. Invest in robust security measures today, including MFA, strong password policies, employee training, advanced threat protection, and regular security audits, to protect your business and its valuable data. Prioritize Office365 security to safeguard your future.

Featured Posts
-
 The Cricket Bat Maker Skill And Heritage
May 23, 2025
The Cricket Bat Maker Skill And Heritage
May 23, 2025 -
 Dan Lawrence England Test Opener Assessing His Chances And Future
May 23, 2025
Dan Lawrence England Test Opener Assessing His Chances And Future
May 23, 2025 -
 Dc Legends Of Tomorrow Character Guide And Strategies
May 23, 2025
Dc Legends Of Tomorrow Character Guide And Strategies
May 23, 2025 -
 Vybz Kartels New York Shows A Night To Remember In Brooklyn
May 23, 2025
Vybz Kartels New York Shows A Night To Remember In Brooklyn
May 23, 2025 -
 Witkoff Alleges Hamas Deception A Key Emissarys Story
May 23, 2025
Witkoff Alleges Hamas Deception A Key Emissarys Story
May 23, 2025
Latest Posts
-
 10 Fastest Standard Production Ferraris Fiorano Circuit Performance
May 24, 2025
10 Fastest Standard Production Ferraris Fiorano Circuit Performance
May 24, 2025 -
 Mamma Mia Unveiling The New Ferrari Hot Wheels Collection
May 24, 2025
Mamma Mia Unveiling The New Ferrari Hot Wheels Collection
May 24, 2025 -
 Fastest Ferraris Ranking The Top 10 Production Cars At Fiorano
May 24, 2025
Fastest Ferraris Ranking The Top 10 Production Cars At Fiorano
May 24, 2025 -
 Hot Wheels Ferrari New Sets A Mamma Mia Experience
May 24, 2025
Hot Wheels Ferrari New Sets A Mamma Mia Experience
May 24, 2025 -
 Ferraris 10 Fastest Production Models Fiorano Track Times
May 24, 2025
Ferraris 10 Fastest Production Models Fiorano Track Times
May 24, 2025
