Cybercriminal's Millions: FBI Probes Office365 Executive Inbox Breaches
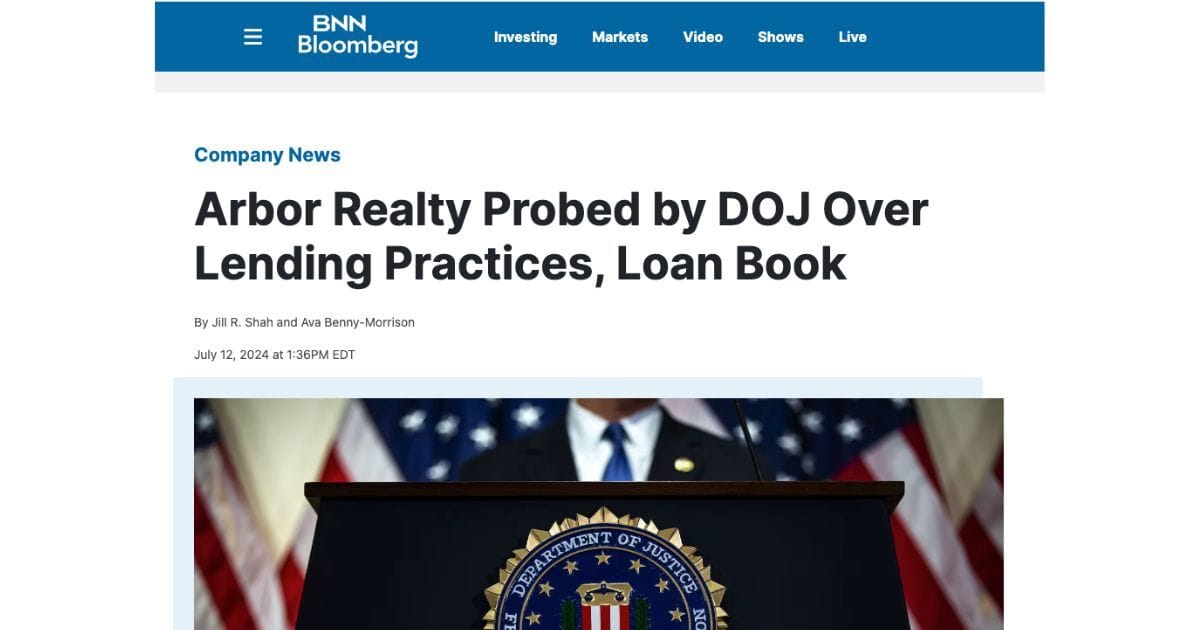
Table of Contents
The Rising Threat of Office365 Executive Inbox Breaches
The number of Office365 executive inbox breaches is escalating rapidly. Executives are prime targets because they often have access to sensitive financial data and the authority to authorize significant transactions, making them valuable assets for cybercriminals. These attacks are becoming increasingly sophisticated, employing a range of tactics to bypass security measures.
- Increased sophistication of phishing emails: Cybercriminals craft highly personalized and convincing phishing emails designed to trick executives into revealing login credentials or clicking malicious links. These emails often mimic legitimate communications from trusted sources.
- Social engineering techniques: Attackers leverage psychological manipulation to gain the trust of executives. This may involve building rapport over time or creating a sense of urgency to pressure victims into making hasty decisions.
- Exploitation of vulnerabilities: While Office 365 itself boasts robust security, vulnerabilities can exist in third-party applications integrated with the platform or in less secure user practices. Cybercriminals actively seek and exploit these weaknesses.
- Malware and ransomware: Successful breaches often involve deploying malware to steal data or ransomware to encrypt sensitive information and demand a ransom for its release. This can lead to significant financial and reputational damage.
FBI Investigation: Scope and Focus
The FBI investigation into Office365 executive inbox breaches is wide-ranging, aiming to understand the scale of the problem and bring perpetrators to justice. While the exact number of affected companies remains confidential for ongoing investigative reasons, reports suggest a significant number of businesses across various sectors have fallen victim.
- Scale of the problem: The FBI's investigation highlights the pervasive nature of these attacks, affecting businesses of all sizes and across numerous industries.
- Types of financial losses: The losses are substantial, encompassing unauthorized wire transfers, fraudulent invoices, and the theft of intellectual property.
- Methods employed: The investigation is focused on uncovering the specific techniques used by cybercriminals, including analyzing malware samples, phishing emails, and compromised accounts.
- Collaboration: The FBI is likely collaborating with other law enforcement agencies nationally and internationally to coordinate efforts and share intelligence.
Methods Used by Cybercriminals
Cybercriminals employ a range of sophisticated techniques to target Office365 executive inbox breaches:
- Spear phishing campaigns: These highly targeted attacks use personalized information to craft convincing phishing emails, increasing the likelihood of success.
- Credential stuffing: Attackers use lists of stolen usernames and passwords obtained from previous data breaches to attempt to gain access to accounts.
- Brute-force attacks: These automated attacks try various combinations of usernames and passwords until they find a match.
- Exploiting third-party vulnerabilities: Cybercriminals often target vulnerabilities in third-party applications integrated with Office 365 to gain unauthorized access.
- Compromised accounts for further attacks: Once an executive's account is compromised, it can be used to launch further attacks against other employees or business partners.
Protecting Your Organization from Office365 Executive Inbox Breaches
Protecting your organization from Office365 executive inbox breaches requires a multi-layered approach:
- Implement multi-factor authentication (MFA): MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if they obtain login credentials.
- Regular security awareness training: Educate employees about phishing techniques and social engineering tactics. Regular training reinforces good security practices.
- Strong password policies: Enforce the use of strong, unique passwords and encourage the use of password management tools.
- User activity monitoring: Monitor user activity for suspicious login attempts and unusual behavior.
- Regular software updates: Keep all software and applications, including Office 365, up-to-date with the latest security patches.
- Invest in advanced threat protection: Consider investing in advanced threat protection solutions that can detect and prevent sophisticated attacks.
Safeguarding Your Business from Office365 Executive Inbox Breaches
The FBI investigation into Office365 executive inbox breaches underscores the significant financial risks associated with these cyberattacks. The methods employed by cybercriminals are evolving constantly, demanding a proactive and comprehensive security strategy. Don't become the next victim of cybercriminal's millions. Implement robust security protocols and protect your Office365 accounts today. Learn more about securing your organization against Office365 executive inbox breaches and other cyber threats. Invest in your security – it's an investment in your future.

Featured Posts
-
 254 Apple Stock Price Forecast A Wall Street Analysts Perspective And Investment Advice
May 24, 2025
254 Apple Stock Price Forecast A Wall Street Analysts Perspective And Investment Advice
May 24, 2025 -
 Porsche Classic Art Week Indonesia 2025 Seni Dan Otomotif Berkolaborasi
May 24, 2025
Porsche Classic Art Week Indonesia 2025 Seni Dan Otomotif Berkolaborasi
May 24, 2025 -
 Amundi Msci World Catholic Principles Ucits Etf Acc Daily Nav And Investment Implications
May 24, 2025
Amundi Msci World Catholic Principles Ucits Etf Acc Daily Nav And Investment Implications
May 24, 2025 -
 Gun Trafficking In Massachusetts 18 Brazilians Charged Over 100 Firearms Confiscated
May 24, 2025
Gun Trafficking In Massachusetts 18 Brazilians Charged Over 100 Firearms Confiscated
May 24, 2025 -
 Atp Indian Wells Drapers Breakthrough Masters 1000 Win
May 24, 2025
Atp Indian Wells Drapers Breakthrough Masters 1000 Win
May 24, 2025
Latest Posts
-
 Top Appliance Deals For Memorial Day 2025 Forbes Recommendations
May 24, 2025
Top Appliance Deals For Memorial Day 2025 Forbes Recommendations
May 24, 2025 -
 The Last Rodeo A Review Of A Familiar Yet Powerful Film
May 24, 2025
The Last Rodeo A Review Of A Familiar Yet Powerful Film
May 24, 2025 -
 Neal Mc Donough Faces Danger In The Last Rodeo Bull Riding Scenes
May 24, 2025
Neal Mc Donough Faces Danger In The Last Rodeo Bull Riding Scenes
May 24, 2025 -
 Damien Darhk Vs Superman Neal Mc Donough On A Potential Dc Return
May 24, 2025
Damien Darhk Vs Superman Neal Mc Donough On A Potential Dc Return
May 24, 2025 -
 Actor Neal Mc Donough Seen At Boises Acero Boards And Bottles
May 24, 2025
Actor Neal Mc Donough Seen At Boises Acero Boards And Bottles
May 24, 2025
