Cybercriminal's Multi-Million Dollar Office365 Executive Email Scheme
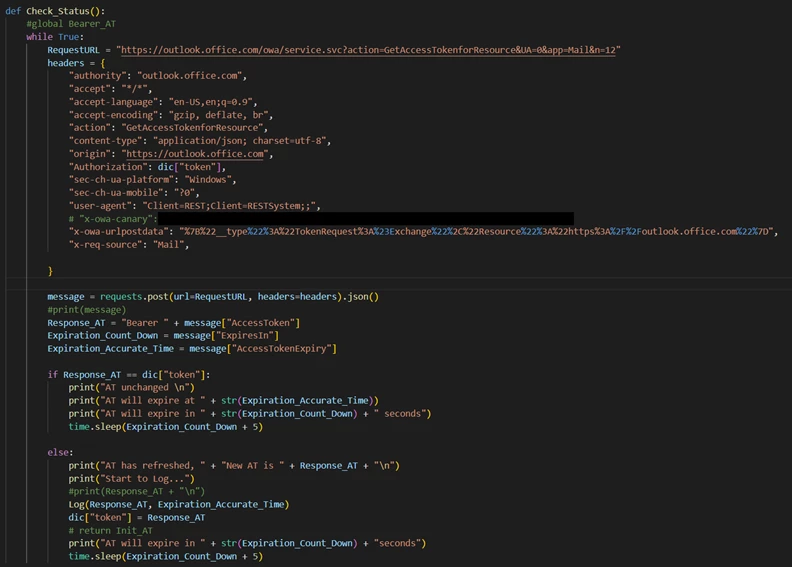
Table of Contents
A shocking statistic: Businesses lose an average of $1.8 million annually due to Office365 Executive Email Compromise (O365 EEC) attacks. This isn't just a theoretical threat; it's a growing epidemic impacting businesses of all sizes. Office365 Executive Email Compromise, or EEC, is a sophisticated form of cybercrime that targets high-level executives within organizations leveraging their access to sensitive financial information and authority. This article will delve into a real-world case study illustrating a multi-million dollar scheme driven by O365 EEC, showcasing the devastating consequences and offering crucial preventative measures.
Understanding the Office365 Executive Email Compromise (O365 EEC) Attack Vector
H3: Phishing and Spoofing Techniques:
O365 EEC attacks heavily rely on highly sophisticated phishing and spoofing techniques. Attackers employ:
- Spear phishing: Highly targeted emails crafted to seem legitimate and personalized to the recipient, often containing details about the company or the executive.
- CEO fraud: Emails that appear to originate from the CEO or another senior executive, instructing employees to execute fraudulent wire transfers or divulge sensitive information.
- Email spoofing: Attackers cleverly mimic legitimate email addresses, making the email appear to come from a trusted source. They often use slight variations in the email address that are difficult to spot at first glance.
- Malicious links and attachments: These can lead to malware infections, credential theft, or redirect victims to fake login pages. The attachments often appear as innocuous documents, invoices or spreadsheets.
H3: Exploiting Weak Security Measures:
Attackers often exploit vulnerabilities in Office365 security:
- Lack of Multi-Factor Authentication (MFA): MFA is a critical layer of security, adding an extra step of verification beyond passwords. Its absence makes it significantly easier for attackers to gain unauthorized access.
- Weak passwords and password reuse: Easily guessable or reused passwords across multiple accounts create an easy entry point for attackers.
- Compromised credentials: Phishing attacks, malware infections, and other methods can result in stolen credentials, granting attackers direct access to Office365 accounts.
- Social engineering: Manipulating employees into revealing sensitive information or bypassing security protocols through psychological manipulation.
The Multi-Million Dollar Scheme: A Case Study of O365 EEC in Action
H3: The Attack Timeline:
In one particular case, attackers successfully compromised an executive's Office365 account through a sophisticated spear-phishing campaign. The email mimicked a request from a known vendor, prompting the executive to approve a seemingly legitimate invoice. This granted the attackers access, allowing them to monitor the executive's communications and identify upcoming wire transfer requests. They then subtly altered an upcoming payment to a fraudulent account. The entire process was completed within days, bypassing all existing internal verification processes.
H3: The Financial Impact:
The attack resulted in a multi-million dollar loss for the victim company. Beyond the immediate financial damage, this included significant reputational damage, legal fees, and a disruption of normal business operations. The long-term consequences of such breaches can severely impact company stability.
H3: The Attacker's Methodology:
The attackers employed advanced techniques to cover their tracks. They used temporary email addresses, encrypted communication channels, and carefully timed actions to avoid detection. Their proficiency highlights the growing sophistication of O365 EEC attacks and the need for robust security measures.
Protecting Your Organization from Office365 Executive Email Compromise
H3: Implementing Robust Security Measures:
Protecting your organization requires a multi-layered approach:
- Mandatory Multi-Factor Authentication (MFA): Implement MFA for all Office365 users, especially executives.
- Strong password policies: Enforce strong, unique passwords and encourage the use of password managers.
- Regular security awareness training: Educate employees on recognizing and avoiding phishing attempts and social engineering tactics.
- Advanced threat protection: Utilize email security solutions that offer advanced threat protection, including anti-spoofing and anti-phishing capabilities.
- Regular security audits and penetration testing: Identify vulnerabilities in your security posture and proactively address them.
H3: Incident Response Planning:
A comprehensive incident response plan is crucial:
- Establish clear communication channels: Designate a team responsible for handling security incidents and ensure swift communication across the organization.
- Develop a step-by-step incident response procedure: Outline the actions to take if an O365 EEC attack is suspected.
- Implement data backup and recovery procedures: Regularly back up your data to mitigate data loss in the event of an attack.
- Collaborate with law enforcement: If necessary, involve law enforcement agencies to investigate the attack and prosecute the perpetrators.
Conclusion: Strengthening Your Defenses Against Office365 Executive Email Compromise
O365 Executive Email Compromise poses a significant threat to businesses of all sizes. The multi-million dollar scheme detailed above illustrates the devastating financial and reputational consequences of such attacks. Proactive security measures, including robust MFA implementation, security awareness training, and advanced threat protection, are crucial in mitigating the risk. A well-defined incident response plan is equally vital to minimize damage if an attack occurs. Protect your business from O365 Executive Email Compromise – take action today! Explore advanced security solutions and training resources available online to fortify your organization's defenses against this growing threat.

Featured Posts
-
 Cp News Alert Ovechkins 894th Goal Ties Gretzkys Nhl Record
May 16, 2025
Cp News Alert Ovechkins 894th Goal Ties Gretzkys Nhl Record
May 16, 2025 -
 Nba Playoffs Celtics Vs Magic Game 1 Live Stream And Tv Schedule
May 16, 2025
Nba Playoffs Celtics Vs Magic Game 1 Live Stream And Tv Schedule
May 16, 2025 -
 Belgica Vs Portugal 0 1 Resumen Completo Y Goles Destacados
May 16, 2025
Belgica Vs Portugal 0 1 Resumen Completo Y Goles Destacados
May 16, 2025 -
 Celtics Vs Magic Game 1 Where To Watch The Nba Playoffs Live
May 16, 2025
Celtics Vs Magic Game 1 Where To Watch The Nba Playoffs Live
May 16, 2025 -
 2024s Most Popular Baby Names Nostalgia And Newness
May 16, 2025
2024s Most Popular Baby Names Nostalgia And Newness
May 16, 2025
