Data Breach Costs Millions: Office365 Executive Accounts Targeted
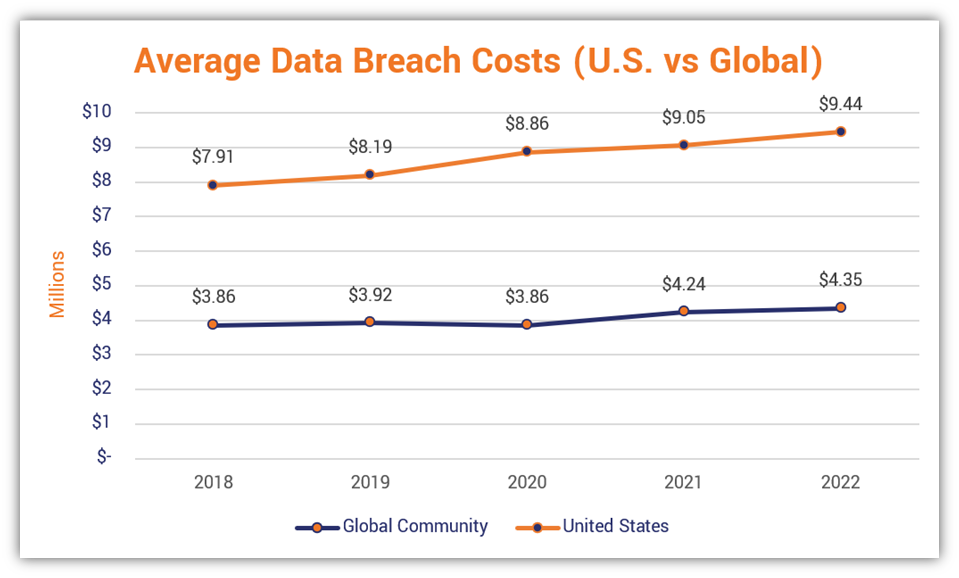
Table of Contents
The High Financial Costs of Office365 Data Breaches
The financial impact of an Office365 data breach, especially one involving executive accounts, can be devastating. Costs aren't limited to immediate expenses; they ripple through the organization, impacting long-term profitability and reputation.
- Direct Costs: These include legal fees (often substantial in the wake of regulatory investigations), regulatory fines (depending on the severity of the breach and compliance regulations like GDPR or CCPA), incident response costs (hiring forensic experts, notifying affected parties, etc.), and system restoration expenses.
- Indirect Costs: These are often far more significant and harder to quantify. They encompass loss of reputation and brand trust, leading to decreased customer loyalty and churn. Productivity is severely impacted during and after a breach, while the cost of recovering stolen intellectual property or restoring compromised business processes can run into the hundreds of thousands or even millions of dollars.
Examples of Financial Losses:
- A recent breach at a Fortune 500 company resulted in over $10 million in direct and indirect costs due to the compromise of executive email accounts, including the theft of sensitive financial data.
- Smaller businesses have faced bankruptcy after suffering breaches resulting in significant data loss and reputational damage, costing them far more than initial recovery efforts.
- The average cost of a data breach involving compromised executive accounts is estimated to be significantly higher than the average cost of a general data breach, often exceeding $5 million due to the sensitive information involved.
Why Executive Office365 Accounts Are Prime Targets
Executive accounts represent a treasure trove of sensitive information for cybercriminals. The privileged access these accounts often possess allows attackers to wreak significant havoc.
- Privileged Access: Executives typically have access to crucial financial data, strategic plans, sensitive customer information, and intellectual property. Compromising an executive account provides attackers a pathway to all of this.
- Business Email Compromise (BEC): BEC attacks target executives to initiate fraudulent wire transfers, manipulate contracts, or steal confidential information by impersonating them in email communications.
- Data Theft and Sabotage: A compromised executive account can be used to steal valuable intellectual property, sabotage systems, or disrupt operations, causing immense damage.
Methods Attackers Use:
- Phishing: Highly targeted phishing emails designed to trick executives into revealing their credentials.
- Malware: Malicious software that infects systems and grants attackers access.
- Credential Stuffing: Using stolen credentials from other breaches to gain access to Office365 accounts.
- Social Engineering: Manipulating executives into revealing sensitive information through various forms of deception.
Sensitive Data Handled by Executives:
- Financial records and transactions
- Mergers and acquisitions plans
- Strategic partnerships and negotiations
- Employee data and payroll information
- Confidential customer data
Effective Strategies to Prevent Office365 Executive Account Breaches
Proactive security measures are paramount in protecting your organization from costly Office365 executive account breaches. A multi-layered approach is essential.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security, requiring more than just a password to access accounts. Implement MFA for all users, especially executives. Consider using different MFA methods for increased security such as hardware security keys or authenticator apps.
- Security Awareness Training: Regular security awareness training, specifically tailored for executives, is crucial. Educate them on phishing tactics, social engineering techniques, and the importance of strong passwords.
- Robust Password Policies: Enforce strong password policies with complexity requirements, regular password changes, and password management tools to help employees create and manage secure passwords.
- Advanced Threat Protection (ATP): Implement Office365 ATP to filter out malicious emails and attachments, and to monitor for suspicious activities within the system.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities and assess the effectiveness of your security measures.
Examples of Proactive Measures:
- Utilize Microsoft Authenticator or Google Authenticator for MFA.
- Implement regular phishing simulations to train employees on recognizing threats.
- Use a password manager like LastPass or 1Password to ensure complex passwords.
- Employ ATP services offered by Microsoft or third-party vendors.
- Schedule penetration tests at least annually with a reputable cybersecurity firm.
The Role of Insider Threats in Office365 Executive Account Compromises
While external threats are significant, insider threats—malicious or negligent employees—can also compromise executive accounts.
- Malicious Insiders: Employees who deliberately misuse their access to steal data or sabotage systems.
- Negligent Insiders: Employees who inadvertently expose sensitive information through carelessness or lack of training.
Mitigating Insider Threats:
- Access Control and Least Privilege: Implement strict access control policies, ensuring that employees only have access to the information and systems necessary to perform their jobs.
- Background Checks: Conduct thorough background checks on all employees, particularly those with access to sensitive data.
- Employee Monitoring (with appropriate legal and ethical considerations): Monitor employee activity to detect suspicious behavior, but always comply with privacy regulations and ethical guidelines.
Examples of Insider Threats and Consequences:
- A disgruntled employee might leak sensitive information to competitors.
- A negligent employee could accidentally share confidential data via an unsecured email.
- An employee with malicious intent could install malware on company systems, granting access to attackers.
Conclusion: Protecting Your Organization from Office365 Executive Account Breaches
The high cost of Office365 executive account breaches, coupled with the increasing sophistication of cyberattacks, demands a proactive and multi-layered approach to security. By understanding the vulnerabilities and implementing the robust security measures outlined above, your organization can significantly reduce its risk. Don't wait until a breach occurs – assess your current security posture, strengthen your defenses, and consider engaging professional cybersecurity consultants to help you create a comprehensive security strategy tailored to your organization's needs. For more information on securing your Office365 environment, explore resources from [mention relevant cybersecurity resources or organizations here]. Protecting your organization from Office365 executive account breaches is an investment that will safeguard your reputation, financial stability, and future success.

Featured Posts
-
 Boston Celtics 6 1 Billion Sale Impact On The Franchise And Its Fans
May 15, 2025
Boston Celtics 6 1 Billion Sale Impact On The Franchise And Its Fans
May 15, 2025 -
 Ovechkin Scores 894 Goals Tying Gretzkys Nhl Record
May 15, 2025
Ovechkin Scores 894 Goals Tying Gretzkys Nhl Record
May 15, 2025 -
 Mlb Dfs May 8th Sleeper Picks Value Plays And One Batter To Avoid
May 15, 2025
Mlb Dfs May 8th Sleeper Picks Value Plays And One Batter To Avoid
May 15, 2025 -
 Biden Rejects Accusations Examining The Evidence
May 15, 2025
Biden Rejects Accusations Examining The Evidence
May 15, 2025 -
 Russell County Town Issues Boil Water Advisory
May 15, 2025
Russell County Town Issues Boil Water Advisory
May 15, 2025
