Exec Office365 Breach: Crook Makes Millions, Feds Say

Table of Contents
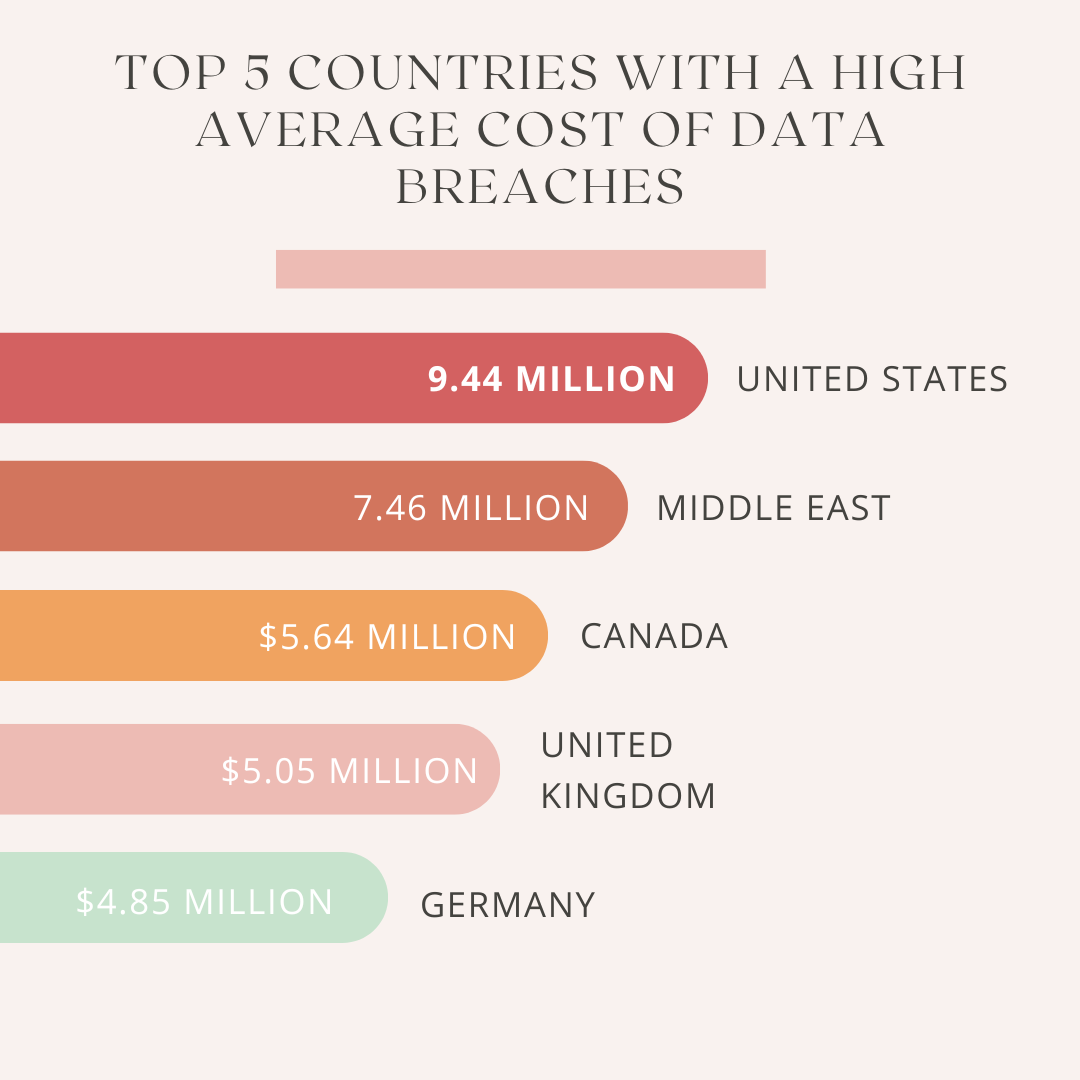
The Scale of the Office365 Breach and Financial Impact
This Office365 data breach resulted in staggering financial losses. While the exact figures released by the FBI remain partially redacted to protect the victimized company, reports indicate the theft of several million dollars. The breach compromised multiple executive accounts, granting the criminals access to sensitive financial information and payment systems. The funds were allegedly transferred through a series of carefully orchestrated wire transfers, exploiting vulnerabilities in the company's internal financial controls.
- Exact figures stolen: While not publicly available, sources suggest millions of dollars were stolen.
- Number of affected accounts: Multiple executive accounts were compromised, giving the criminals wide-ranging access.
- Methods of fund transfer: The criminals utilized wire transfers, highlighting the ease with which large sums of money can be moved digitally.
- Impact on the company: The breach caused significant reputational damage and operational disruption, impacting investor confidence and requiring substantial resources for remediation and investigation.
The long-term consequences for the affected company could include legal battles, loss of investor trust, and a decline in market share. The broader impact extends to the erosion of business confidence in the security of cloud-based systems and the increased scrutiny placed on Office365 security protocols.
The Method of the Office365 Breach: How Did It Happen?
The FBI investigation points to a sophisticated phishing attack as the primary method of entry. The criminals used social engineering techniques to target executive accounts, leveraging the trust placed in high-ranking personnel. The phishing emails contained malicious links or attachments that delivered malware onto the victim's systems. This malware then allowed the criminals to steal credentials and move laterally within the network.
- Techniques used: The attack involved a multi-pronged approach combining spear-phishing emails, sophisticated malware, and exploitation of known Office365 vulnerabilities.
- Access to executive accounts: The criminals likely targeted executives due to their access to sensitive financial information and approval authority for transactions.
- Multi-factor authentication (MFA) bypass: Reports suggest that MFA protocols were either not implemented or were successfully bypassed, highlighting the critical importance of strong MFA practices.
- Effectiveness of security measures: The breach exposed weaknesses in the company's existing security measures, emphasizing the need for more robust security protocols and regular security audits.
The attackers likely exploited known vulnerabilities in older versions of Office365 software or leveraged weaknesses in the company’s security policies. This underscores the importance of patching software regularly, implementing strong password policies, and utilizing multi-factor authentication to enhance security.
The FBI Investigation and Legal Ramifications
The FBI launched a comprehensive investigation immediately following the report of the Office365 breach. The timeline included forensic analysis of the compromised systems, tracing the flow of stolen funds, and identifying the perpetrators. While details remain under seal, reports suggest significant progress in the investigation.
- Timeline of the investigation: The investigation is ongoing, but early stages included securing evidence from the victim's systems and identifying the methods used in the attack.
- Arrests and charges: While specifics are unavailable at this time due to ongoing proceedings, the FBI has indicated arrests are likely to follow.
- Relevant laws and regulations: This case falls under various cybersecurity laws, including those dealing with financial fraud and data theft, resulting in potentially severe penalties.
- Legal penalties: The perpetrator(s) face significant prison time and substantial financial penalties.
Lessons Learned and Best Practices for Office365 Security
This Office365 data breach serves as a stark reminder of the importance of proactive cybersecurity measures. Organizations must prioritize their security posture to protect themselves from similar attacks.
- Strong passwords and MFA: Implementing and enforcing strong password policies and multi-factor authentication are crucial first steps.
- Regular security audits: Conduct regular security assessments and penetration testing to identify and address vulnerabilities.
- Security awareness training: Invest in comprehensive security awareness training for all employees to educate them about phishing and other social engineering tactics.
- Robust data loss prevention (DLP) measures: Implement DLP measures to monitor and control the movement of sensitive data within and outside the organization.
By investing in these security best practices, businesses can significantly reduce their risk of an Office365 breach and protect their valuable data and financial assets.
Conclusion
The Office365 breach described here resulted in significant financial losses and exposed critical vulnerabilities in the victim's security posture. This incident highlights the need for robust cybersecurity measures, including strong password policies, multi-factor authentication, regular security audits, and comprehensive security awareness training for all employees. The perpetrators face severe legal consequences, underscoring the gravity of these crimes. Protect your business from an Office365 breach. Implement robust cybersecurity measures, invest in security awareness training, and ensure your organization is adequately protected against sophisticated attacks. Learn more about bolstering your Office365 security today!

Featured Posts
-
 Damen And Icdas Turkish Tugboat Project Announced
Apr 26, 2025
Damen And Icdas Turkish Tugboat Project Announced
Apr 26, 2025 -
 Open Ais Chat Gpt The Ftc Investigation And Its Potential Fallout
Apr 26, 2025
Open Ais Chat Gpt The Ftc Investigation And Its Potential Fallout
Apr 26, 2025 -
 Mission Impossibles Final Chapter A Look At Missing Sequels
Apr 26, 2025
Mission Impossibles Final Chapter A Look At Missing Sequels
Apr 26, 2025 -
 Why Middle Management Matters A Comprehensive Look At Their Impact
Apr 26, 2025
Why Middle Management Matters A Comprehensive Look At Their Impact
Apr 26, 2025 -
 Sunken Wwii Warship Reveals Well Preserved Car
Apr 26, 2025
Sunken Wwii Warship Reveals Well Preserved Car
Apr 26, 2025
Latest Posts
-
 Ev Mandate Faces Renewed Opposition From Car Dealers
Apr 27, 2025
Ev Mandate Faces Renewed Opposition From Car Dealers
Apr 27, 2025 -
 Resistance Mounts Car Dealerships Push Back On Ev Mandate
Apr 27, 2025
Resistance Mounts Car Dealerships Push Back On Ev Mandate
Apr 27, 2025 -
 Auto Dealers Double Down On Opposition To Ev Sales Targets
Apr 27, 2025
Auto Dealers Double Down On Opposition To Ev Sales Targets
Apr 27, 2025 -
 Car Dealers Renew Fight Against Electric Vehicle Mandates
Apr 27, 2025
Car Dealers Renew Fight Against Electric Vehicle Mandates
Apr 27, 2025 -
 Fbi Investigation Major Office365 Data Breach Results In Significant Financial Losses
Apr 27, 2025
Fbi Investigation Major Office365 Data Breach Results In Significant Financial Losses
Apr 27, 2025
