Federal Investigation: Millions Stolen Via Executive Office365 Account Breaches
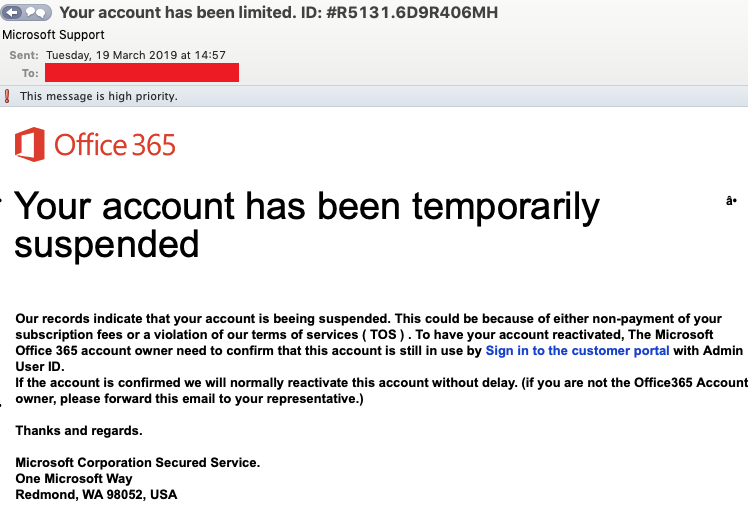
Table of Contents
The Scale of the Problem: Financial Losses and Data Compromises
The federal investigation into Executive Office 365 account breaches is revealing a disturbing trend: sophisticated cyberattacks are targeting businesses through seemingly secure platforms. The financial impact is staggering. While precise figures from the ongoing investigation remain undisclosed, sources suggest losses in the millions of dollars for numerous affected organizations.
Financial Impact
- Significant Direct Losses: The direct theft of funds is only the tip of the iceberg. Millions have been stolen through fraudulent transactions facilitated by access to compromised accounts.
- Increased Operational Costs: The investigation, remediation efforts (including data recovery and legal fees), and the potential loss of productivity all contribute to significant operational overheads.
- Reputational Damage & Stock Price Impacts: Public disclosure of a data breach can severely damage a company’s reputation, impacting customer trust and potentially leading to a decline in stock prices for publicly traded companies. The loss of investor confidence can result in further substantial financial losses.
Data Breach Implications
Beyond the direct financial losses, the consequences of Executive Office 365 account breaches extend to the sensitive data potentially exposed. Compromised accounts can offer attackers access to a wealth of information:
- Customer Personal Information: Names, addresses, phone numbers, email addresses, and potentially even credit card details are highly valuable to identity thieves and fraudsters.
- Intellectual Property: Confidential business plans, research data, and proprietary software can be stolen, giving competitors a significant advantage.
- Financial Records: Access to financial data, including bank accounts and transactions, enables further financial crimes.
These breaches can lead to significant regulatory fines under laws such as GDPR and CCPA, further adding to the financial burden. The damage to customer trust and brand reputation can also take years to repair.
Methods of Attack: How Executive Office 365 Accounts Were Breached
The attackers involved in these Executive Office 365 account breaches employ a range of sophisticated techniques:
Phishing and Social Engineering
A primary method used in these attacks is phishing, often employing sophisticated social engineering tactics.
- Deceptive Emails: Attackers send emails mimicking legitimate communications from trusted sources, such as internal IT departments or banking institutions. Subject lines often create a sense of urgency or importance, luring unsuspecting users into clicking malicious links.
- Credential Harvesting: These links often lead to fake login pages designed to steal usernames and passwords. Sophisticated phishing campaigns might even leverage compromised internal email accounts to send more convincing phishing messages within the organization.
- Impersonation: Social engineering often involves impersonating colleagues or superiors to manipulate employees into revealing sensitive information or granting access.
Exploiting Software Vulnerabilities
Attackers may also exploit known vulnerabilities in Office 365 software. Staying updated with security patches is crucial.
- Zero-Day Exploits: While less common, attacks might leverage newly discovered, unpatched vulnerabilities (zero-day exploits) to gain unauthorized access.
- Outdated Software: Failing to update Office 365 software to the latest versions leaves systems vulnerable to known exploits.
- Importance of MFA: Multi-factor authentication (MFA) is a critical layer of defense, making it significantly harder for attackers to access accounts even if they obtain credentials.
Credential Stuffing and Brute-Force Attacks
Attackers frequently use stolen credentials from other platforms to try accessing Office 365 accounts (credential stuffing). They may also attempt brute-force attacks, systematically trying various password combinations.
- Password Reuse: Reusing passwords across multiple platforms significantly increases the risk of account compromise.
- Weak Passwords: Easily guessable passwords are highly vulnerable to brute-force attacks.
- Account Lockout Policies: Implementing robust account lockout policies helps to mitigate brute-force attempts.
Preventing Executive Office 365 Account Breaches: Best Practices for Businesses
Protecting your organization from Executive Office 365 account breaches requires a multi-layered approach:
Implementing Robust Security Measures
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security, requiring users to provide a second form of verification (like a code from their phone) in addition to their password.
- Strong Password Policies: Enforce strong, unique passwords and encourage the use of password managers.
- Security Awareness Training: Regularly train employees on recognizing and avoiding phishing attempts and other social engineering tactics.
- Advanced Threat Protection: Implement advanced threat protection solutions to monitor for and block malicious activity.
Regular Security Audits and Penetration Testing
- Regular Security Assessments: Conduct regular security audits and penetration testing to identify and address vulnerabilities before they can be exploited. A proactive approach is far more cost-effective than reacting to a breach.
- Incident Response Planning: Develop and regularly test an incident response plan to effectively manage and mitigate the impact of a security breach. This plan should outline clear steps to contain the breach, investigate its causes, and recover from the attack.
Conclusion
The ongoing federal investigation into Executive Office 365 account breaches underscores the devastating financial and reputational consequences of neglecting cybersecurity. Millions have already been lost, and the potential for further damage remains significant. Don't become the next victim of Executive Office 365 account breaches. Implement robust security measures, including multi-factor authentication, strong password policies, regular security awareness training, and advanced threat protection. Regular security audits and penetration testing are also crucial for identifying and mitigating vulnerabilities. Consider consulting with cybersecurity professionals to tailor a comprehensive security strategy to your specific needs. Protecting your business from these threats is not just a good idea—it's a necessity.

Featured Posts
-
 Functioneert Een Bio Based Basisschool Zonder Generator
May 01, 2025
Functioneert Een Bio Based Basisschool Zonder Generator
May 01, 2025 -
 Understanding The 9 Key Differences Between Target And Standalone Starbucks
May 01, 2025
Understanding The 9 Key Differences Between Target And Standalone Starbucks
May 01, 2025 -
 Noodgeneratoren Voor Bio Based Scholen Een Noodzakelijke Investering
May 01, 2025
Noodgeneratoren Voor Bio Based Scholen Een Noodzakelijke Investering
May 01, 2025 -
 Ireland Faces Stiff Test After Frances Six Nations Victory Over Italy
May 01, 2025
Ireland Faces Stiff Test After Frances Six Nations Victory Over Italy
May 01, 2025 -
 Gia Tieu Hom Nay Tang Manh Nong Dan Phan Khoi
May 01, 2025
Gia Tieu Hom Nay Tang Manh Nong Dan Phan Khoi
May 01, 2025
Latest Posts
-
 Thunder Over Louisville 2024 Fireworks Show Cancellation Announcement Due To Flooding
May 01, 2025
Thunder Over Louisville 2024 Fireworks Show Cancellation Announcement Due To Flooding
May 01, 2025 -
 Thunder Over Louisville Fireworks Show Canceled Ohio River Flooding
May 01, 2025
Thunder Over Louisville Fireworks Show Canceled Ohio River Flooding
May 01, 2025 -
 State Of Emergency In Louisville Following Devastating Tornado Flood Warnings Issued
May 01, 2025
State Of Emergency In Louisville Following Devastating Tornado Flood Warnings Issued
May 01, 2025 -
 Remembering Tragedy Louisville Residents Under Shelter In Place Order
May 01, 2025
Remembering Tragedy Louisville Residents Under Shelter In Place Order
May 01, 2025 -
 Louisvilles Shelter In Place Lessons From Past Events
May 01, 2025
Louisvilles Shelter In Place Lessons From Past Events
May 01, 2025
