High-Profile Office365 Data Breach Costs Businesses Millions
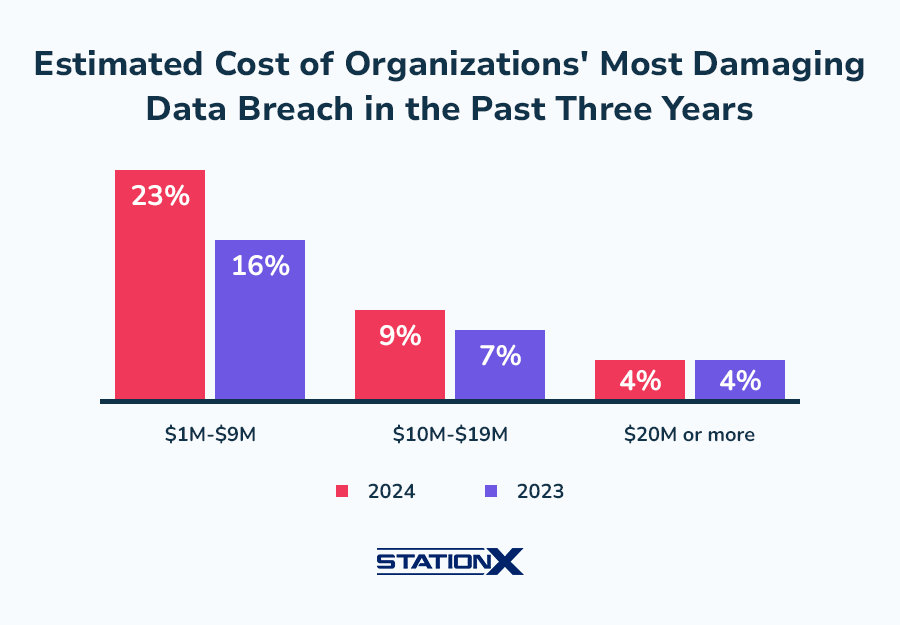
Table of Contents
The Rising Tide of Office365 Data Breaches
The frequency and severity of Office365 data breaches are alarming. Attackers are constantly developing new and innovative ways to exploit vulnerabilities, making it crucial for businesses to understand the risks and implement robust security measures.
Common Attack Vectors
Cybercriminals employ various methods to breach Office365 security. Here are some of the most prevalent:
-
Phishing: This remains the most successful attack vector. Malicious emails disguised as legitimate communications trick employees into revealing credentials or downloading malware. Statistics show that a significant percentage of successful breaches begin with a phishing attack. For example, a recent Verizon Data Breach Investigations Report highlighted phishing as the leading cause of data breaches across various industries.
-
Credential Stuffing: Attackers use stolen usernames and passwords from other platforms to attempt to gain access to Office365 accounts. This often works because employees frequently reuse passwords across multiple services.
-
Malware: Malicious software can be downloaded through phishing emails, infected attachments, or compromised websites, granting attackers access to sensitive data stored within Office365. Ransomware attacks targeting Office365 data are increasingly common.
-
Exploiting Third-Party App Vulnerabilities: Many businesses integrate third-party applications with Office365, creating potential vulnerabilities if these apps are not properly secured. A compromised third-party app can provide a backdoor into the entire Office365 environment.
The High Cost of Data Breaches
The financial consequences of an Office365 data breach can be devastating. Costs include:
-
Legal Fees: Responding to a data breach involves significant legal costs, including investigations, notifications, and potential litigation.
-
Regulatory Fines: Failure to comply with regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) can result in substantial fines.
-
Remediation Costs: Recovering from a breach requires investing in IT security experts, forensic analysis, and system restoration, adding significant costs.
-
Loss of Customers: A data breach can severely damage a company's reputation, leading to a loss of customers and business opportunities. IBM's Cost of a Data Breach Report consistently shows a strong correlation between data breaches and customer churn.
-
Reputational Damage: The negative publicity associated with a data breach can have long-term effects on a company's brand image and market value.
-
Increased Insurance Premiums: After a breach, insurance companies often raise premiums, reflecting the increased risk.
Understanding Vulnerabilities in Your Office365 Environment
Identifying weaknesses within your Office365 environment is crucial for effective security.
Weak Passwords and Phishing Susceptibility
Many breaches stem from weak passwords and susceptibility to phishing. Strengthening these areas is paramount.
-
Best Practices for Password Management: Implement strong password policies requiring complex passwords, regular changes, and password managers.
-
Effective Phishing Awareness Training: Regularly train employees to identify and avoid phishing attempts through simulated phishing campaigns and educational materials. Statistics show that employee training significantly reduces the success rate of phishing attacks.
-
Multi-Factor Authentication (MFA): MFA adds an extra layer of security, significantly reducing the risk of unauthorized access, even if credentials are compromised. Studies show MFA drastically decreases successful account takeovers.
Unpatched Software and Third-Party App Risks
Outdated software and unsecured third-party apps are major vulnerabilities.
-
Software Patching Process: Establish a regular process for patching all software and applications, including Office365 itself and integrated third-party tools.
-
Third-Party App Vetting: Carefully vet all third-party applications before integration, ensuring they meet security standards and regularly update their security measures. Consider using a secure app store or conducting thorough security assessments before integrating any third-party app.
Protecting Your Business from Office365 Data Breaches
Proactive measures are essential to protect your organization.
Implementing Robust Security Measures
Several key security measures can bolster your Office365 defenses:
-
Multi-Factor Authentication (MFA): Essential for all users accessing Office365.
-
Advanced Threat Protection (ATP): Provides enhanced protection against sophisticated phishing attacks and malware.
-
Data Loss Prevention (DLP): Helps prevent sensitive data from leaving your organization's control.
-
Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities.
The Role of Employee Training and Awareness
Employee training is critical in preventing breaches.
-
Key Elements of a Security Awareness Program: Include regular phishing simulations, security awareness training modules, and clear communication of security policies.
-
Creating Engaging Training Materials: Use interactive training methods, such as videos and quizzes, to improve engagement and retention.
Incident Response Planning
Having a comprehensive incident response plan is crucial.
-
Key Components of an Effective Incident Response Plan: Establish clear roles and responsibilities, communication protocols, and procedures for containing and remediating a breach.
-
Resources for Developing an Incident Response Plan: Utilize available resources, including cybersecurity frameworks like NIST Cybersecurity Framework, to guide your plan creation.
Conclusion
The cost of an Office365 data breach can be financially and reputationally crippling. By understanding common attack vectors, strengthening your security posture through robust measures like MFA and ATP, implementing comprehensive employee training programs, and developing a robust incident response plan, you can significantly reduce the risk. Don't become another statistic – protect your business from costly Office365 data breaches today! Invest in thorough security assessments and proactive security solutions to secure your Office365 environment now! Contact a cybersecurity expert to discuss your specific needs and implement a tailored security strategy.

Featured Posts
-
 Graeme Souness Reveals His Premier League Favourite Player
May 03, 2025
Graeme Souness Reveals His Premier League Favourite Player
May 03, 2025 -
 Sony Play Station Beta Program Registration Now Open Requirements Inside
May 03, 2025
Sony Play Station Beta Program Registration Now Open Requirements Inside
May 03, 2025 -
 Offshore Wind Farm Development Facing Headwinds From High Costs
May 03, 2025
Offshore Wind Farm Development Facing Headwinds From High Costs
May 03, 2025 -
 The Trump Tariffs And The Limits Of Judicial Power
May 03, 2025
The Trump Tariffs And The Limits Of Judicial Power
May 03, 2025 -
 Justice Departments Decision To End School Desegregation A Turning Point
May 03, 2025
Justice Departments Decision To End School Desegregation A Turning Point
May 03, 2025
Latest Posts
-
 Expert Prediction Souness Names Arsenals Top Champions League Rival
May 03, 2025
Expert Prediction Souness Names Arsenals Top Champions League Rival
May 03, 2025 -
 Arsenal Faces Stiff Champions League Competition Sounesss Expert Analysis
May 03, 2025
Arsenal Faces Stiff Champions League Competition Sounesss Expert Analysis
May 03, 2025 -
 Souness Issues Stark Arsenal Warning Unbeatable Champions League Rival Emerges
May 03, 2025
Souness Issues Stark Arsenal Warning Unbeatable Champions League Rival Emerges
May 03, 2025 -
 Graeme Souness Arsenal Warning Another Champions League Contender Soars
May 03, 2025
Graeme Souness Arsenal Warning Another Champions League Contender Soars
May 03, 2025 -
 Drone Attack On Gaza Freedom Flotilla Ship Sos Signal Issued Near Malta
May 03, 2025
Drone Attack On Gaza Freedom Flotilla Ship Sos Signal Issued Near Malta
May 03, 2025
