Massive Office365 Data Breach Results In Multi-Million Dollar Loss

Table of Contents
The Cost of an Office365 Data Breach: More Than Just Dollars and Cents
An Office365 data breach extends far beyond the immediate financial losses. The total cost encompasses a web of direct and indirect expenses that can cripple even the most robust organizations.
Direct Financial Losses
The immediate financial impact of an Office365 data breach is substantial and multifaceted:
- Legal fees and regulatory fines: Non-compliance with regulations like GDPR, CCPA, and others can lead to crippling fines. The penalties are directly tied to the severity of the breach and the number of affected individuals.
- Costs associated with incident response and remediation: Hiring cybersecurity experts, forensic investigators, and legal counsel to contain the breach, investigate its cause, and implement remediation measures adds up quickly.
- Loss of revenue due to business disruption: A significant data breach can halt operations, leading to lost sales, project delays, and a significant impact on productivity.
- Costs of credit monitoring and identity theft protection for affected customers: Offering credit monitoring and identity theft protection services to affected customers is a crucial step in mitigating reputational damage, but it represents a considerable expense.
- Data recovery and restoration expenses: Recovering and restoring lost or compromised data can be incredibly complex and costly, especially if backups are inadequate or unavailable.
Indirect Financial Losses
The indirect costs of an Office365 data breach can be equally devastating, often exceeding the direct costs over time:
- Reputational damage and loss of customer trust: A data breach severely erodes customer trust, potentially leading to a loss of customers and future business. This damage can be long-lasting and difficult to repair.
- Decreased stock value and investor confidence: For publicly traded companies, a data breach can trigger a significant drop in stock value, eroding investor confidence and impacting future funding opportunities.
- Increased insurance premiums: Following a data breach, insurance premiums for cybersecurity and liability coverage are likely to increase dramatically.
- Loss of intellectual property and competitive advantage: The theft of intellectual property can give competitors a significant edge and severely damage a company's competitive position.
- Impact on future business opportunities: A damaged reputation can significantly impact a company's ability to win new business and secure future contracts.
Common Vulnerabilities Leading to Office365 Data Breaches
Several vulnerabilities can lead to devastating Office365 data breaches. Understanding these weaknesses is crucial for implementing effective security measures.
Phishing and Social Engineering Attacks
Phishing emails and social engineering tactics remain highly effective in exploiting human error. These attacks often impersonate legitimate organizations, tricking users into revealing their credentials or downloading malicious software.
- Example: Emails appearing to be from Microsoft, requesting password resets or urgent account verification.
- Mitigation: Comprehensive employee cybersecurity awareness training is crucial to recognize and avoid these attacks. Regular phishing simulations help employees identify suspicious emails.
Weak or Shared Passwords
Using weak passwords or reusing passwords across multiple accounts is incredibly risky. Compromising one account can provide access to many others.
- Mitigation: Enforce strong password policies, requiring unique, complex passwords for each account. Implement and enforce multi-factor authentication (MFA) for all users.
Unpatched Software and Vulnerable Applications
Outdated software and applications contain known vulnerabilities that cybercriminals can exploit.
- Mitigation: Regularly update and patch all Office365 applications and related software. Utilize automated patching solutions where possible to ensure timely updates.
Third-Party Application Vulnerabilities
Integrating third-party applications without proper vetting can introduce vulnerabilities into your Office365 environment.
- Mitigation: Carefully vet all third-party applications before integrating them. Use secure application access management solutions to control and monitor access to these applications.
Protecting Your Organization from an Office365 Data Breach
Proactive measures are vital to protect your organization from a costly Office365 data breach.
Implementing Robust Security Measures
Implementing robust security measures is paramount in preventing breaches. This includes:
- Multi-factor authentication (MFA): Mandate MFA for all users to add an extra layer of security.
- Regular security awareness training: Regular training keeps employees informed about the latest threats and best practices.
- Strong password policies and enforcement: Enforce strong password complexity requirements and regularly review and update policies.
- Data loss prevention (DLP) tools and strategies: Implement DLP tools to monitor and prevent sensitive data from leaving the organization's control.
- Regular security audits and penetration testing: Regular audits and penetration testing identify vulnerabilities and weaknesses before attackers can exploit them.
- Microsoft's advanced threat protection features: Leverage Microsoft's built-in security features, such as advanced threat protection, to enhance your security posture.
Developing an Incident Response Plan
Having a well-defined incident response plan is crucial for minimizing the impact of a breach. This plan should include:
- Clearly defined steps: Outline the steps to take in case of a data breach, including immediate containment, investigation, and remediation.
- Communication plan: A detailed communication plan to inform affected parties and stakeholders is essential.
- Expertise: Identify and establish relationships with legal and cybersecurity experts who can assist during a breach.
Conclusion
The financial and reputational consequences of a massive Office365 data breach are far-reaching and potentially catastrophic. Understanding the common vulnerabilities and implementing robust security measures, including MFA, regular security training, and a comprehensive incident response plan, are crucial for protecting your organization. Don't let an Office365 data breach cripple your business – invest in robust security measures today. Proactive protection is far less costly than the aftermath of a multi-million dollar data loss.

Featured Posts
-
 The Best John Wick Movie A Rotten Tomatoes Score Paradox
May 07, 2025
The Best John Wick Movie A Rotten Tomatoes Score Paradox
May 07, 2025 -
 Did Skype Get It Right An Examination Of Its Predictions
May 07, 2025
Did Skype Get It Right An Examination Of Its Predictions
May 07, 2025 -
 Jenna Ortegas Verdict On A Small Mcu Role Revival
May 07, 2025
Jenna Ortegas Verdict On A Small Mcu Role Revival
May 07, 2025 -
 Steve Kerr Provides Update On Stephen Currys Injury Return
May 07, 2025
Steve Kerr Provides Update On Stephen Currys Injury Return
May 07, 2025 -
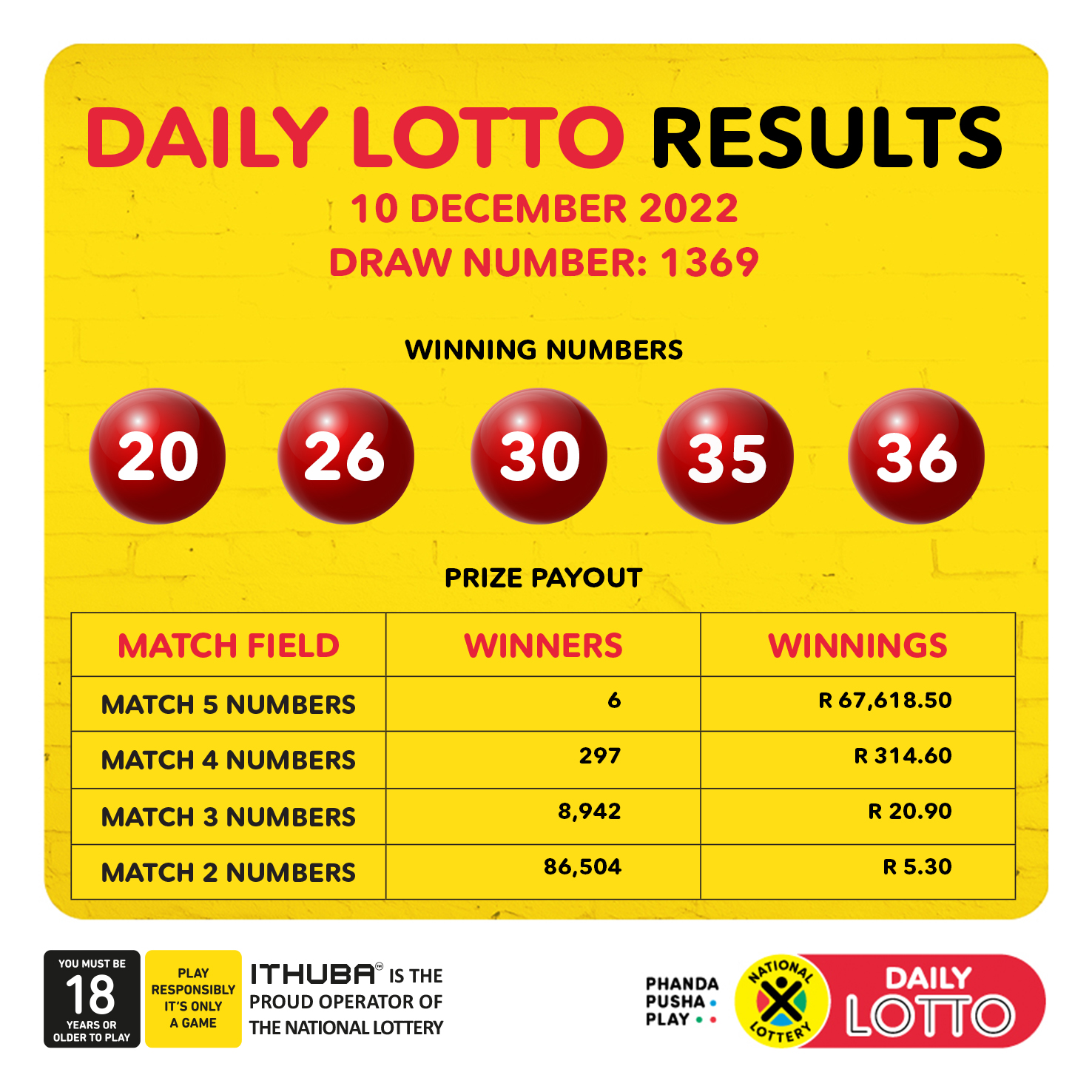 Daily Lotto Results For Thursday 17th April 2025
May 07, 2025
Daily Lotto Results For Thursday 17th April 2025
May 07, 2025
Latest Posts
-
 Jenna Ortegas Departure From Scream The Real Reason After Barreras Exit
May 07, 2025
Jenna Ortegas Departure From Scream The Real Reason After Barreras Exit
May 07, 2025 -
 Why Did Jenna Ortega Leave The Scream Franchise Following Melissa Barrera
May 07, 2025
Why Did Jenna Ortega Leave The Scream Franchise Following Melissa Barrera
May 07, 2025 -
 Jenna Ortega And Glen Powells Upcoming Film What We Know
May 07, 2025
Jenna Ortega And Glen Powells Upcoming Film What We Know
May 07, 2025 -
 Jenna Ortegas Scream Exit Why She Left After Melissa Barrera
May 07, 2025
Jenna Ortegas Scream Exit Why She Left After Melissa Barrera
May 07, 2025 -
 Jenna Ortega And Glen Powell A New Movie Collaboration
May 07, 2025
Jenna Ortega And Glen Powell A New Movie Collaboration
May 07, 2025
