Millions Made From Executive Office365 Account Hacks: Federal Investigation
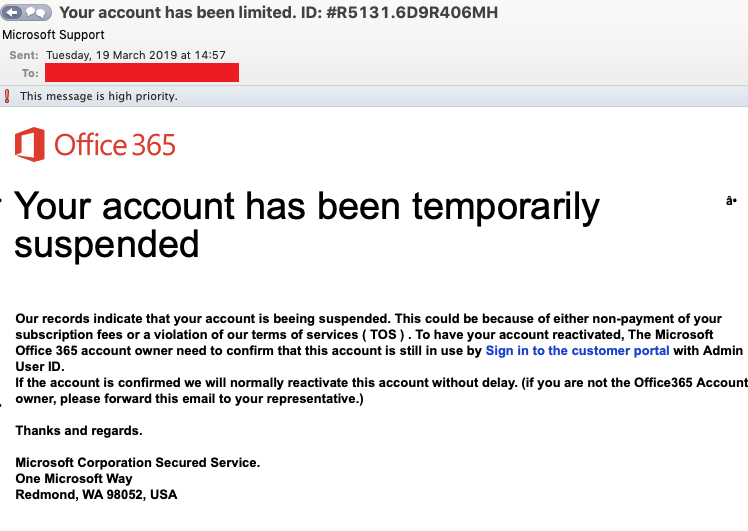
Table of Contents
A staggering $50 million in financial losses has been attributed to a wave of sophisticated Office 365 account hacks targeting high-level executives. This alarming trend has prompted a significant federal investigation, shedding light on the vulnerability of even the most secure accounts. The victims include CEOs, CFOs, and other high-ranking officials from diverse industries, raising concerns about both financial repercussions and potential national security implications. This article will delve into the methods, motivations, and consequences of these Executive Office365 Account Hacks, providing insights into the ongoing investigation and offering crucial advice on bolstering your security.
The Tactics Used in Executive Office365 Account Compromises
Phishing and Spear Phishing Attacks
Phishing and spear phishing attacks are the primary methods used in these Executive Office365 Account Hacks. Attackers craft personalized emails designed to mimic legitimate communications from trusted sources, often exploiting the executive's familiarity with specific individuals or companies. These sophisticated social engineering techniques exploit psychological vulnerabilities, leading even the most cautious individuals to click malicious links or download infected attachments.
- Personalized Emails: Attackers meticulously research their targets, crafting emails tailored to their roles and interests.
- Deceptive Tactics: Urgent requests, threats, or promises of significant financial gains are used to manipulate victims.
- Successful Examples: Recent high-profile cases highlight the effectiveness of these attacks, with even seasoned executives falling victim to well-crafted phishing schemes. These attacks often leverage current events or industry news to increase credibility.
- Keyword Integration: "Office 365 phishing," "executive email compromise," "spear phishing techniques," "CEO email fraud"
Credential Stuffing and Brute-Force Attacks
Beyond phishing, attackers utilize stolen credentials obtained from data breaches on other platforms to attempt access to Executive Office365 accounts via credential stuffing. This involves systematically testing compromised username and password combinations against Office 365 logins. Additionally, brute-force attacks attempt to guess passwords through automated trial and error.
- Credential Stuffing: Stolen credentials from unrelated websites are used to gain access. Dark web marketplaces are often the source of these credentials.
- Brute-Force Attacks: While slower, brute-force attacks can be successful against weak passwords.
- Password Security: Implementing strong, unique passwords for every account is crucial. Password managers can assist with this.
- Keyword Integration: "credential stuffing," "brute force attacks," "Office 365 password security," "password manager"
Exploiting Vulnerabilities in Third-Party Apps
Many organizations integrate third-party applications into their Office 365 environment, which can unfortunately introduce security vulnerabilities. Attackers can exploit weaknesses in these apps to gain unauthorized access to accounts.
- Third-Party App Risks: Poorly secured third-party apps can act as entry points for attackers.
- Vulnerability Exploitation: Attackers search for and exploit known vulnerabilities in these applications.
- Due Diligence: Thorough vetting of third-party apps, including security audits and reviews, is essential.
- Keyword Integration: "Office 365 third-party app security," "vulnerability exploitation," "app security risks," "API security"
The Financial Ramifications of Executive Office365 Account Breaches
Direct Financial Losses
The financial consequences of Executive Office365 Account Hacks are severe. Direct losses include:
- Stolen Funds: Attackers can directly transfer funds from compromised accounts.
- Intellectual Property Theft: Confidential business information, trade secrets, and other valuable intellectual property can be stolen.
- Financial Impact Examples: News reports reveal multi-million dollar losses in some cases.
- Keyword Integration: "financial impact of data breaches," "Office 365 data loss cost," "cybercrime financial losses," "business email compromise cost"
Reputational Damage and Legal Costs
Beyond direct financial losses, breaches lead to significant reputational damage and hefty legal costs.
- Reputational Damage: Loss of customer trust, damage to brand image, and difficulty attracting investors.
- Legal Costs: Lawsuits from affected customers, regulatory fines, and legal fees associated with investigations.
- Keyword Integration: "reputational damage," "cybersecurity legal costs," "data breach litigation," "brand reputation management"
The Federal Investigation and Its Implications
The Scope of the Investigation
The federal investigation into Executive Office365 Account Hacks is wide-ranging, involving multiple agencies.
- Agencies Involved: The FBI, CISA, and other relevant agencies are likely involved.
- Investigation Goals: Identifying perpetrators, disrupting criminal networks, and preventing future attacks.
- Potential Consequences: Significant penalties, including imprisonment and substantial fines, await those found responsible.
- Keyword Integration: "federal investigation," "cybersecurity enforcement," "Office 365 account hacking investigation," "cybercrime prosecution"
Potential Legislative Changes
The scale of these hacks is driving legislative changes aimed at strengthening cybersecurity practices.
- Cybersecurity Legislation: New laws and regulations may mandate stricter security measures for organizations.
- Data Breach Regulations: Increased reporting requirements and penalties for data breaches are likely.
- Office 365 Security Compliance: Organizations may face stricter compliance standards for their Office 365 deployments.
- Keyword Integration: "cybersecurity legislation," "data breach regulations," "Office 365 security compliance," "data protection laws"
Conclusion: Protecting Your Executive Office365 Accounts from Millions in Losses
The sophistication and financial impact of Executive Office365 Account Hacks underscore the urgent need for robust cybersecurity measures. Attackers employ increasingly advanced techniques to compromise accounts, resulting in devastating financial and reputational consequences. This federal investigation highlights the critical importance of proactive security.
To prevent becoming a victim, executives and organizations must implement strong security practices, including:
- Multi-factor authentication (MFA)
- Regular security awareness training for all employees
- Robust incident response plans
- Careful vetting of third-party applications
Don't become another statistic – take action today to protect your Executive Office365 accounts and prevent millions in losses. Invest in comprehensive cybersecurity solutions and stay informed about the latest threats to safeguard your organization's valuable data and reputation.

Featured Posts
-
 Securing Funding For A 270 M Wh Bess Project In The Belgian Merchant Market
May 04, 2025
Securing Funding For A 270 M Wh Bess Project In The Belgian Merchant Market
May 04, 2025 -
 Ufc 314 Volkanovski Vs Lopes Fight Card Breakdown
May 04, 2025
Ufc 314 Volkanovski Vs Lopes Fight Card Breakdown
May 04, 2025 -
 Meet Bianca Censoris Sister Angelina Exploring Her Instagram
May 04, 2025
Meet Bianca Censoris Sister Angelina Exploring Her Instagram
May 04, 2025 -
 Kanye West And Bianca Censori The Fallout And The Flight
May 04, 2025
Kanye West And Bianca Censori The Fallout And The Flight
May 04, 2025 -
 Complete Ufc Schedule For May 2025 Featuring Ufc 315
May 04, 2025
Complete Ufc Schedule For May 2025 Featuring Ufc 315
May 04, 2025
