Millions Stolen: Inside The Office365 Executive Email Breach

Table of Contents
The staggering financial losses from Office365 executive email breaches are reaching epidemic proportions. In 2023 alone, businesses globally lost millions, if not billions, due to sophisticated attacks targeting high-level employees. These aren't simple phishing scams; these are highly targeted, meticulously planned operations designed to exploit vulnerabilities within the seemingly secure environment of Microsoft Office365. This article will delve into the frightening reality of these breaches, exploring the methods used, the devastating impact on organizations, and, most importantly, the steps you can take to protect your business. We'll examine the threat landscape, the consequences of a successful attack, and provide actionable strategies to significantly enhance your Office365 security posture.
Understanding the Office365 Executive Email Compromise Threat
How BEC Attacks Target Executives
Business Email Compromise (BEC) attacks specifically target high-ranking employees because they often have access to sensitive financial information and authority to authorize transactions. Attackers leverage the trust placed in executives to gain access to company funds or sensitive data. They rely heavily on the "trust factor," expertly impersonating executives or vendors to manipulate employees into taking actions that compromise security. Urgency is another key tactic; attackers often create a sense of immediacy to pressure victims into making hasty decisions.
- Common BEC attack vectors:
- Spoofing: Attackers forge emails to mimic legitimate senders, using similar email addresses and logos.
- Phishing emails: These emails contain malicious links or attachments designed to install malware or steal credentials.
- Compromised accounts: Attackers may gain access to legitimate accounts through phishing or exploiting vulnerabilities in other systems.
Statistics consistently show a significant increase in successful BEC attacks, with average losses per incident reaching tens of thousands, and often exceeding millions of dollars. The Anti-Phishing Working Group reports a substantial rise in BEC-related financial losses year over year.
The Role of Social Engineering in Office365 Breaches
Social engineering plays a crucial role in Office365 breaches. Attackers manipulate employees psychologically, leveraging their trust and emotions to obtain sensitive information or initiate actions that benefit the attacker. This often bypasses technical security measures, highlighting the importance of human factors in cybersecurity.
- Common social engineering tactics:
- Pretexting: Creating a false scenario to justify the request for information.
- Baiting: Offering something enticing (like a free gift card) to lure victims into clicking a malicious link.
- Quid pro quo: Offering something in exchange for information or a favor.
These tactics are particularly effective within the Office365 environment, where employees frequently interact with emails and attachments from both internal and external sources.
Common Vulnerabilities in Office365 Security
Many organizations unknowingly leave gaps in their Office365 security, creating easy inroads for attackers. These vulnerabilities often stem from a lack of awareness or inadequate security measures.
- Common Office365 security weaknesses:
- Weak passwords: Easily guessable passwords provide an easy entry point for attackers.
- Lack of multi-factor authentication (MFA): MFA adds an extra layer of security, making it much harder for attackers to access accounts even if they have a password.
- Inadequate security awareness training: Employees who lack training are more susceptible to phishing and social engineering tactics.
- Outdated software: Failing to update software leaves systems vulnerable to known exploits.
The Impact of an Office365 Executive Email Breach
Financial Losses and Reputational Damage
The financial consequences of a successful Office365 executive email breach can be devastating. Losses extend beyond immediate monetary theft; they encompass the costs of investigation, remediation, and recovery.
- Examples of financial losses:
- Wire fraud: Attackers redirect funds to their accounts through fraudulent wire transfers.
- Intellectual property theft: Confidential data, including trade secrets and customer information, can be stolen.
The reputational damage can be equally significant, eroding customer trust and impacting shareholder value. A single breach can lead to a loss of confidence and lasting damage to brand reputation.
Legal and Regulatory Consequences
Data breaches often trigger legal and regulatory repercussions, particularly under regulations like the GDPR. Organizations face potential legal actions from affected individuals and regulatory bodies.
- Potential consequences:
- Legal actions: Lawsuits from affected individuals and businesses.
- Regulatory fines: Significant penalties imposed by regulatory bodies for non-compliance.
- Compliance issues: Difficulty meeting industry standards and regulatory requirements.
Failure to comply with relevant legal frameworks and standards can result in severe penalties and long-term damage.
Operational Disruptions
Beyond financial and legal ramifications, a successful breach can cause significant operational disruptions, impacting productivity and business continuity.
- Examples of operational disruptions:
- System downtime: Systems may need to be taken offline for investigation and remediation.
- Data recovery: Recovering lost or compromised data can be a time-consuming and costly process.
These disruptions can lead to lost revenue, decreased productivity, and strained customer relationships.
Protecting Your Organization from Office365 Email Breaches
Implementing Robust Security Measures
Proactive measures are critical in preventing Office365 email breaches. Implementing a multi-layered security approach is vital.
- Essential security measures:
- Enable MFA: Multi-factor authentication significantly reduces the risk of unauthorized access.
- Implement strong password policies: Enforce the use of complex, unique passwords.
- Use advanced threat protection: Leverage Office 365's advanced threat protection features.
- Conduct regular security awareness training: Educate employees about phishing, social engineering, and other threats.
- Segment networks: Restrict access to sensitive data by segmenting your network.
The Importance of Employee Training
Employee training is paramount in preventing breaches. Employees are often the weakest link in the security chain.
- Effective training strategies:
- Regular phishing simulations: Test employees' ability to identify phishing emails.
- Security awareness training programs: Provide comprehensive training on cybersecurity best practices.
- Clear communication protocols: Establish clear procedures for reporting suspicious emails and incidents.
Utilizing Advanced Security Tools
Investing in advanced security tools can significantly enhance your protection against sophisticated attacks.
- Examples of advanced security tools:
- Email security gateways: Filter malicious emails before they reach users' inboxes.
- Intrusion detection systems (IDS): Monitor network traffic for suspicious activity.
- Security information and event management (SIEM) systems: Collect and analyze security logs to detect and respond to threats.
Conclusion
Office365 executive email breaches represent a significant and growing threat to businesses worldwide. The methods employed are sophisticated, the consequences are devastating, and the financial and reputational impact can be long-lasting. By understanding the vulnerabilities, implementing robust security measures, and providing comprehensive employee training, organizations can significantly reduce their risk. Don't wait until it's too late. Protect your business from costly Office365 email breaches today! Bolster your Office365 security now: Don't become the next victim! Secure your organization's future: Invest in robust Office365 email security.

Featured Posts
-
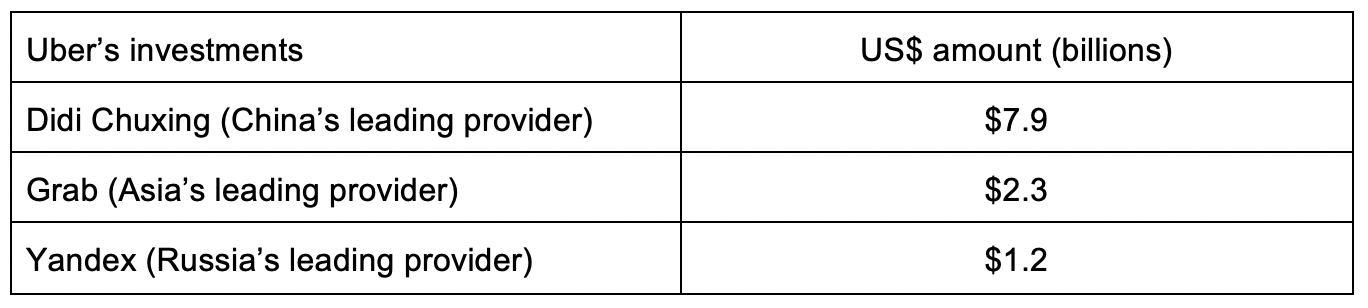 Evaluating Uber Technologies Uber As An Investment
May 17, 2025
Evaluating Uber Technologies Uber As An Investment
May 17, 2025 -
 Best Australian Crypto Casinos A 2025 Guide
May 17, 2025
Best Australian Crypto Casinos A 2025 Guide
May 17, 2025 -
 Megaloprepis Ypodoxi I Afiksi Toy Tramp Stin Saoydiki Aravia
May 17, 2025
Megaloprepis Ypodoxi I Afiksi Toy Tramp Stin Saoydiki Aravia
May 17, 2025 -
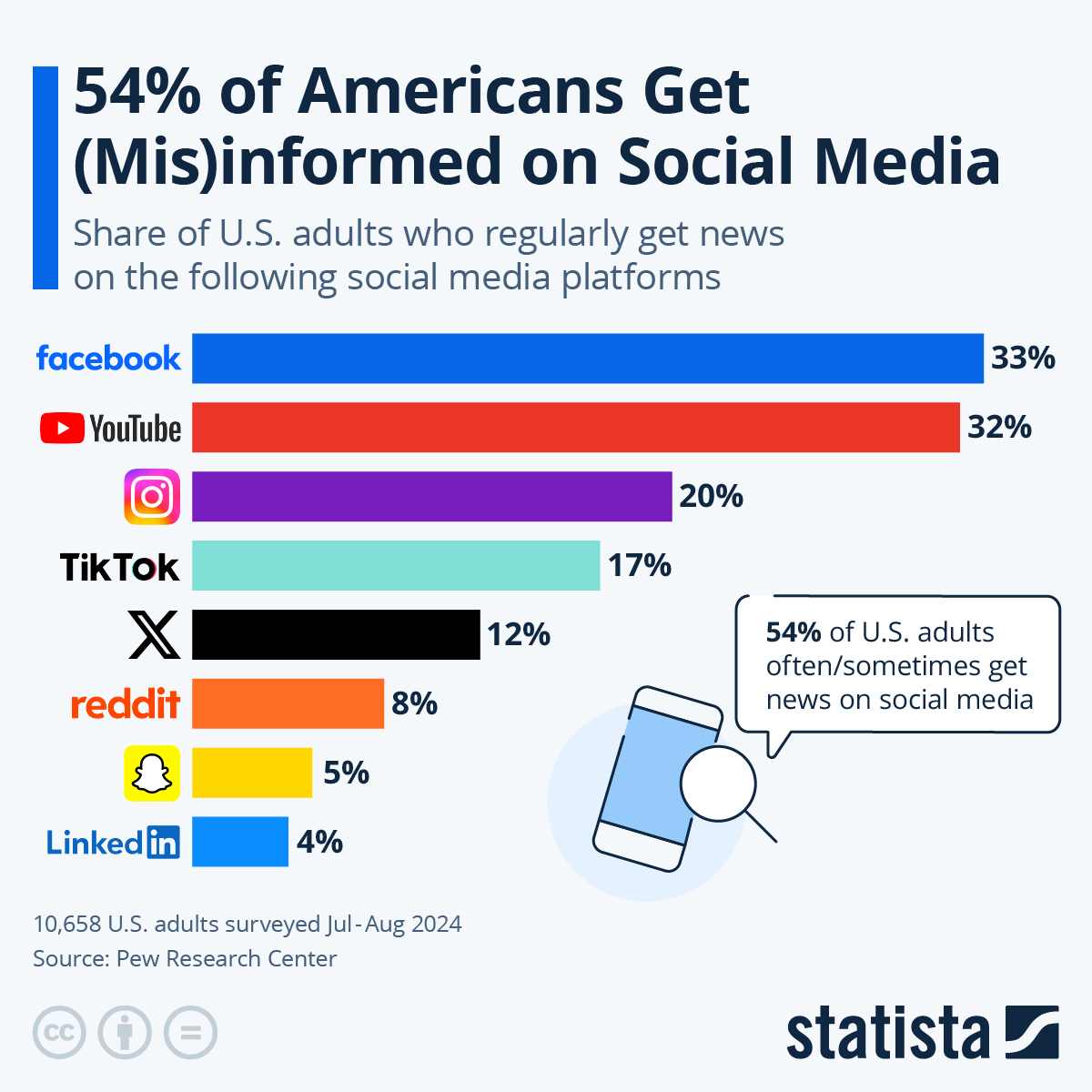 Fake Angel Reese Quotes How Misinformation Spreads Online
May 17, 2025
Fake Angel Reese Quotes How Misinformation Spreads Online
May 17, 2025 -
 Tam Krwz Awr Mdah Ka Jwtwn Ka Waqeh Tfsylat Awr Wayrl Wydyw
May 17, 2025
Tam Krwz Awr Mdah Ka Jwtwn Ka Waqeh Tfsylat Awr Wayrl Wydyw
May 17, 2025
