Office365 Data Breach: Millions Stolen, Suspect Charged
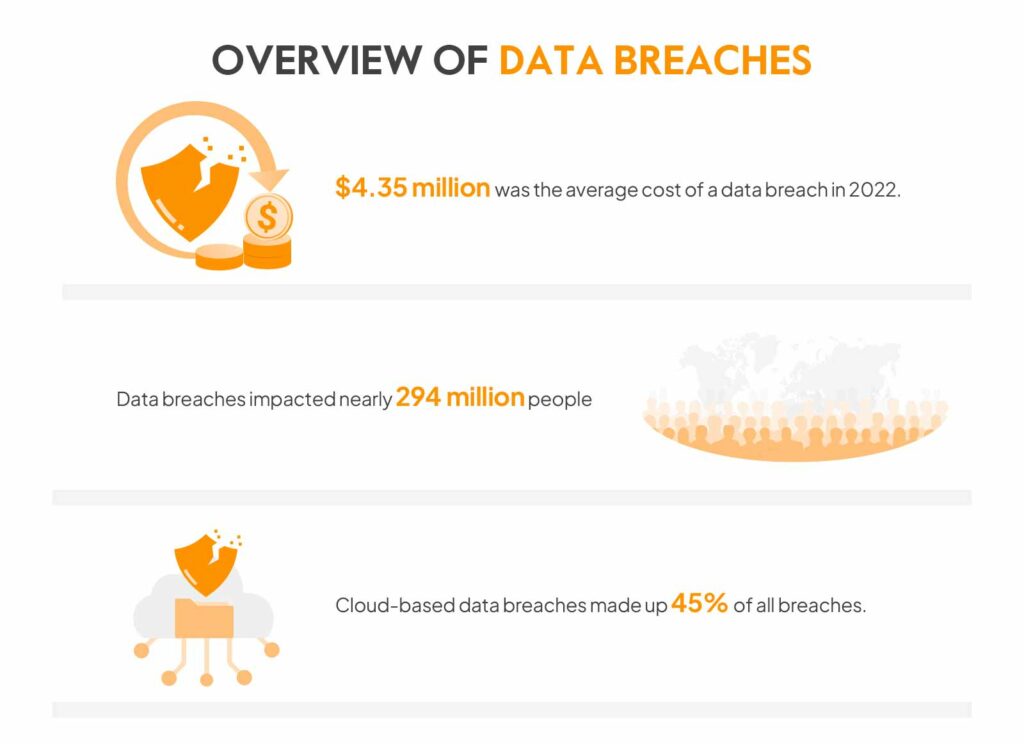
Table of Contents
Scale and Scope of the Office365 Data Breach
The Office365 data breach affected an estimated [Insert Number] users and organizations globally, representing a significant data loss incident. The geographical spread was widespread, with victims reported across [mention regions/countries]. The types of data compromised were extensive, including:
- Emails and email attachments containing confidential communications.
- Calendar data exposing scheduling and meeting details.
- Documents and files, including sensitive business plans, financial records, and intellectual property.
- Customer data, such as personal contact information, addresses, and financial details.
- Employee data, potentially including payroll information and social security numbers.
This data theft highlights the vulnerability of even the most widely used platforms and underscores the critical need for enhanced data protection strategies. The sheer volume of sensitive information lost in this Office365 security breach represents a significant cybersecurity incident with potentially long-lasting consequences. The scale of this data loss is truly alarming.
Methods Used in the Office365 Data Breach
The suspect allegedly gained unauthorized access through a sophisticated combination of techniques, exploiting vulnerabilities in Office365 security. These methods included:
- Phishing attacks: Deceptive emails were sent, designed to trick users into revealing their login credentials.
- Credential stuffing: The suspect used stolen credentials obtained from other breaches to attempt to log into Office365 accounts.
- Exploitation of known vulnerabilities: The suspect may have exploited security flaws in Office365 itself or in related applications.
- Social engineering: The suspect may have manipulated employees into divulging sensitive information or granting access.
The investigation is ongoing, but preliminary findings suggest a multi-stage attack, highlighting the increasingly complex nature of modern cybercrime and the need for advanced threat detection measures to prevent future Office365 security breaches.
The Arrest and Legal Ramifications
Law enforcement authorities recently arrested [Suspect's name – if public; otherwise, use a generic description like "a suspect"] in [Location] and charged them with [Specific charges, e.g., computer fraud, data theft, identity theft]. The ongoing investigation is expected to reveal further details about the methods employed and the full extent of the damage. The legal ramifications for the suspect are substantial, potentially including lengthy prison sentences and hefty fines. Affected organizations may also face legal repercussions, including lawsuits from affected individuals and regulatory penalties for data breach non-compliance. This Office365 data breach investigation underscores the serious legal implications of cybercrime.
Preventing Future Office365 Data Breaches
Protecting your organization and yourself from future Office365 data breaches requires a multi-faceted approach encompassing strong security protocols and employee training:
- Implement multi-factor authentication (MFA): MFA adds an extra layer of security, significantly reducing the risk of unauthorized access, even if credentials are compromised.
- Use strong and unique passwords: Employ strong, complex passwords and change them regularly. Avoid reusing passwords across different accounts.
- Keep software updated: Regularly update your Office365 applications and operating systems to patch security vulnerabilities.
- Conduct regular security awareness training: Educate employees about phishing scams, social engineering tactics, and other cybersecurity threats.
- Enforce strict access control policies: Limit access to sensitive data only to authorized personnel.
- Implement robust data loss prevention (DLP) tools: Use DLP tools to monitor and control the flow of sensitive data.
By following these Office365 security tips and implementing robust cybersecurity best practices, you can significantly reduce your risk of falling victim to a similar Office365 data breach and strengthen your overall data protection.
Conclusion: Safeguarding Your Data from Office365 Data Breaches
The massive Office365 data breach highlights the vulnerability of even the most secure-seeming systems. The scale of the breach, the sophisticated methods used, and the subsequent arrest of a suspect underscore the urgent need for proactive cybersecurity measures. Don't become the next victim of an Office365 data breach. Strengthen your Office 365 security today by implementing the best practices outlined above. Regularly review your Office365 security settings, stay vigilant against phishing attempts, and invest in comprehensive data protection strategies to prevent future Office 365 data breaches. Protecting your sensitive data is paramount – take action now.

Featured Posts
-
 Linda Evangelistas Cool Sculpting Lawsuit The Impact Of Cosmetic Procedure Side Effects
Apr 25, 2025
Linda Evangelistas Cool Sculpting Lawsuit The Impact Of Cosmetic Procedure Side Effects
Apr 25, 2025 -
 Metas Future Under A Trump Administration Zuckerbergs Challenges
Apr 25, 2025
Metas Future Under A Trump Administration Zuckerbergs Challenges
Apr 25, 2025 -
 The High Cost Of Imports A Montreal Guitar Makers Story
Apr 25, 2025
The High Cost Of Imports A Montreal Guitar Makers Story
Apr 25, 2025 -
 Spider Man 4 The Sadie Sink Casting Theory Explained
Apr 25, 2025
Spider Man 4 The Sadie Sink Casting Theory Explained
Apr 25, 2025 -
 Delhis Petrol Car Ban A Model For Other Indian Cities
Apr 25, 2025
Delhis Petrol Car Ban A Model For Other Indian Cities
Apr 25, 2025
Latest Posts
-
 3 Dias Para Comenzar Tu Entrenamiento De Boxeo En Edomex
Apr 30, 2025
3 Dias Para Comenzar Tu Entrenamiento De Boxeo En Edomex
Apr 30, 2025 -
 10 2025 2
Apr 30, 2025
10 2025 2
Apr 30, 2025 -
 Faltan 3 Dias Inscribete A Tus Clases De Boxeo En Edomex
Apr 30, 2025
Faltan 3 Dias Inscribete A Tus Clases De Boxeo En Edomex
Apr 30, 2025 -
 10 2025
Apr 30, 2025
10 2025
Apr 30, 2025 -
 Clases De Boxeo Edomex Inscribete Antes De Que Se Agoten Las Plazas 3 Dias
Apr 30, 2025
Clases De Boxeo Edomex Inscribete Antes De Que Se Agoten Las Plazas 3 Dias
Apr 30, 2025
