Office365 Executive Email Compromise Nets Millions For Hacker, Say Federal Authorities
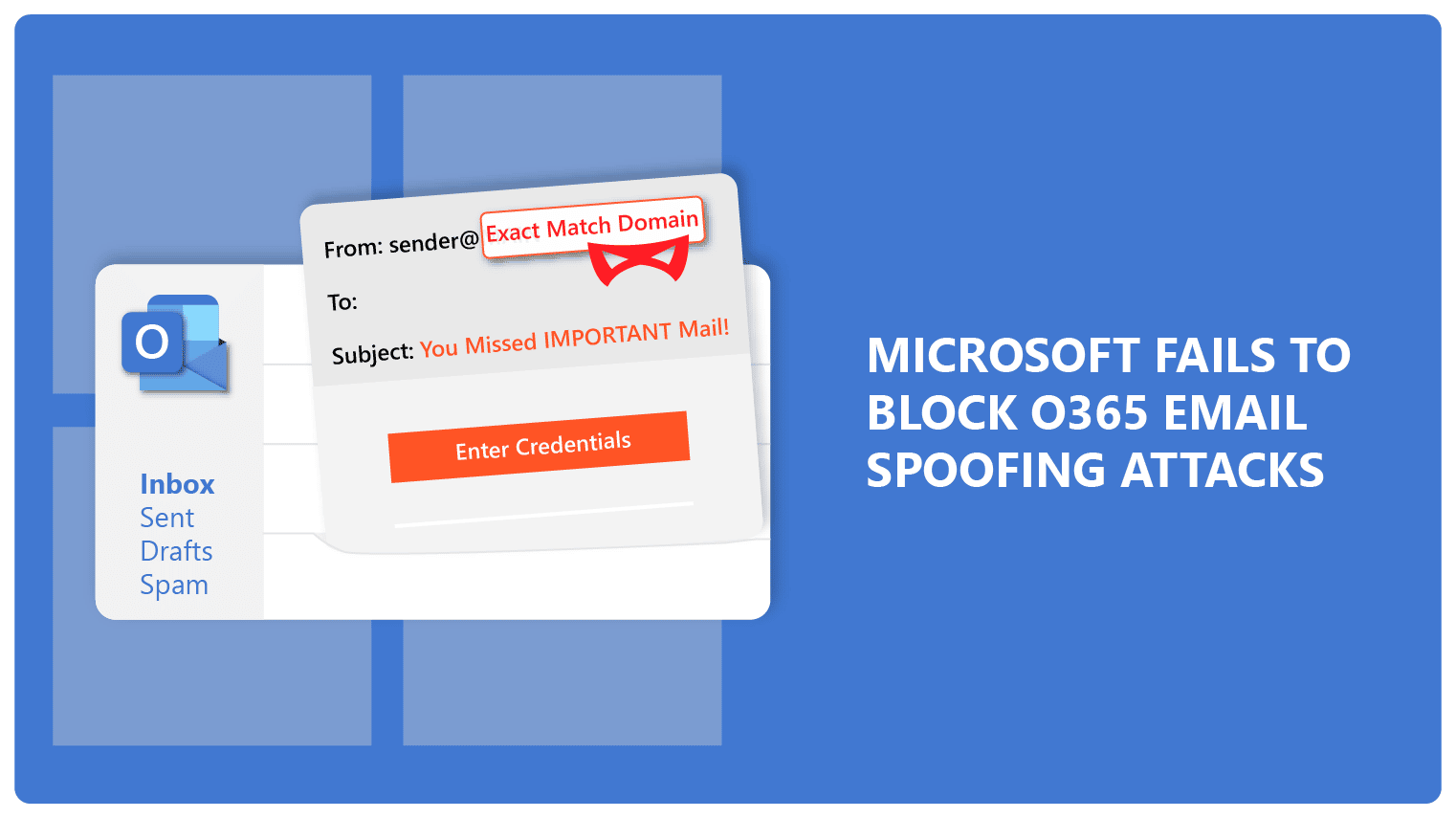
Table of Contents
The Mechanics of the Office365 Executive Email Compromise
The attack likely leveraged several sophisticated techniques commonly employed in Advanced Persistent Threats (APTs). Targeting executives specifically, rather than employing a mass-phishing approach, significantly increases the success rate. Let's break down the likely stages:
- Spear Phishing: The attackers likely used spear phishing, crafting highly personalized emails designed to mimic legitimate communications from trusted sources. These emails often contain urgent requests, compelling the recipient to act quickly without verifying the sender's authenticity.
- Credential Stuffing: Once the initial phishing email is sent, attackers may utilize credential stuffing. This involves using lists of stolen usernames and passwords obtained from previous data breaches to attempt to log into the executive's Office365 account.
- Multi-Factor Authentication (MFA) Bypass: The success of this attack likely hinges on the absence or weakness of multi-factor authentication (MFA). MFA adds an extra layer of security, requiring a second form of verification beyond just a password. Bypassing MFA often requires more sophisticated techniques and social engineering.
- Social Engineering: Sophisticated social engineering techniques may have been deployed to manipulate the executive into revealing their credentials or circumventing security protocols. This could involve building rapport or exploiting psychological vulnerabilities.
- Malware Deployment: Once access is gained, attackers often deploy malware, such as keyloggers or remote access trojans (RATs), to maintain persistent access to the compromised account. This allows for exfiltration of sensitive data, including financial information and intellectual property. The malware may also enable further attacks within the organization's network. This sustained access is a hallmark of Advanced Persistent Threats (APTs).
The difference between targeted (spear phishing) and general phishing attacks lies in their precision. General phishing campaigns cast a wide net, sending mass emails hoping for a few successful compromises. Spear phishing, however, is highly targeted, relying on detailed reconnaissance and personalized messaging to maximize its effectiveness. Identifying these attacks often requires a keen eye for inconsistencies in sender information, email content, and unusual requests.
The Financial Impact of the Office365 Breach
The financial consequences of this Office365 breach were severe, resulting in millions of dollars in losses. These losses were not limited to direct monetary theft, but also encompassed substantial indirect costs:
- Ransomware Attack: The attackers may have demanded a ransom in exchange for the return of data or to prevent further damage. Ransomware attacks are a growing threat, often targeting organizations with valuable data.
- Data Theft: The exfiltration of sensitive data exposes the organization to further financial losses, including potential legal liabilities. This stolen data can be sold on the dark web or used for identity theft.
- Fraudulent Wire Transfers: Attackers may have used the compromised accounts to initiate fraudulent wire transfers, directly diverting funds from the organization's accounts. This is a common tactic used in executive email compromise attacks.
- Reputation Damage: The damage to the organization's reputation can lead to lost business, decreased customer confidence, and difficulty attracting investors.
- Legal Costs: The organization faces significant legal costs associated with responding to the breach, including investigations, regulatory compliance, and potential lawsuits. Data breach notification laws vary across jurisdictions and can lead to considerable expenses.
The long-term consequences of a data breach, including potential regulatory fines (such as GDPR fines in Europe), can significantly impact an organization's financial health for years to come. Reputation management and regaining customer trust are often protracted and costly processes.
Protecting Your Organization from Office365 Executive Email Compromise
Protecting your organization from Office365 executive email compromise requires a multi-layered approach encompassing technology, training, and robust security policies:
- Multi-Factor Authentication (MFA): Implement and enforce robust multi-factor authentication (MFA) across all Office365 accounts. This is a critical first step in preventing unauthorized access, even if credentials are compromised.
- Advanced Email Security Solutions: Invest in advanced email security solutions that incorporate anti-phishing and anti-malware filters, along with sandboxing capabilities to analyze suspicious attachments and links before they reach user inboxes. Consider solutions offering advanced threat protection and URL rewriting.
- Security Awareness Training: Conduct regular, engaging security awareness training for all employees, with a strong focus on phishing and social engineering tactics. Training should simulate real-world scenarios and emphasize the importance of skepticism and verification.
- Threat Intelligence: Leverage threat intelligence feeds to stay informed about emerging threats and vulnerabilities. This proactive approach allows organizations to identify potential risks and adapt their security measures accordingly.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan to minimize the impact of a potential breach. This plan should outline steps to be taken in the event of a security incident, including containment, recovery, and communication strategies.
- Regular Security Audits: Regular security audits and penetration testing are crucial for identifying vulnerabilities in your systems and processes before attackers can exploit them.
Specific examples of email security solutions include Microsoft Defender for Office 365, Proofpoint, and Mimecast. For security awareness training, consider platforms like KnowBe4 and SANS Institute.
Conclusion
The recent Office365 executive email compromise demonstrates the significant financial and reputational risks associated with inadequate cybersecurity measures. Sophisticated cyberattacks targeting high-value individuals within organizations are becoming increasingly common, highlighting the urgency for proactive security strategies. The financial impact extends far beyond direct monetary loss, encompassing legal fees, reputational damage, and the long-term costs of recovery. Don't become the next victim of an Office365 executive email compromise. Invest in robust email security solutions, implement multi-factor authentication, and provide comprehensive security awareness training for your employees. Protecting your organization from these devastating attacks requires a multifaceted approach. Learn more about strengthening your Office365 security today and safeguard your business from the crippling effects of executive email compromise.

Featured Posts
-
 The Ramiro Helmeyer Story A Blaugrana Journey
Apr 27, 2025
The Ramiro Helmeyer Story A Blaugrana Journey
Apr 27, 2025 -
 Una Favorita Se Despide De Indian Wells Analisis Del Resultado
Apr 27, 2025
Una Favorita Se Despide De Indian Wells Analisis Del Resultado
Apr 27, 2025 -
 El Sistema Alberto Ardila Olivares Garantia De Logro En El Futbol
Apr 27, 2025
El Sistema Alberto Ardila Olivares Garantia De Logro En El Futbol
Apr 27, 2025 -
 Canadian Travel Boycott Real Time Impact On The Us Economy
Apr 27, 2025
Canadian Travel Boycott Real Time Impact On The Us Economy
Apr 27, 2025 -
 Analysis The Probability Of A Fifth Premier League Champions League Qualification Spot
Apr 27, 2025
Analysis The Probability Of A Fifth Premier League Champions League Qualification Spot
Apr 27, 2025
Latest Posts
-
 German Politics Crumbachs Resignation And Its Implications For The Spd
Apr 27, 2025
German Politics Crumbachs Resignation And Its Implications For The Spd
Apr 27, 2025 -
 Bsw Leader Crumbachs Resignation Impact On The Spd Coalition
Apr 27, 2025
Bsw Leader Crumbachs Resignation Impact On The Spd Coalition
Apr 27, 2025 -
 Concerns Raised Over Hhss Appointment Of Anti Vaccine Activist To Study Debunked Autism Vaccine Theories
Apr 27, 2025
Concerns Raised Over Hhss Appointment Of Anti Vaccine Activist To Study Debunked Autism Vaccine Theories
Apr 27, 2025 -
 Hhs Under Fire For Selecting Anti Vaccine Advocate To Investigate Autism Vaccine Link
Apr 27, 2025
Hhs Under Fire For Selecting Anti Vaccine Advocate To Investigate Autism Vaccine Link
Apr 27, 2025 -
 Hhss Controversial Choice Anti Vaccine Advocate To Examine Debunked Autism Vaccine Claims
Apr 27, 2025
Hhss Controversial Choice Anti Vaccine Advocate To Examine Debunked Autism Vaccine Claims
Apr 27, 2025
