Office365 Executive Inboxes Targeted In Multi-Million Dollar Hacking Scheme
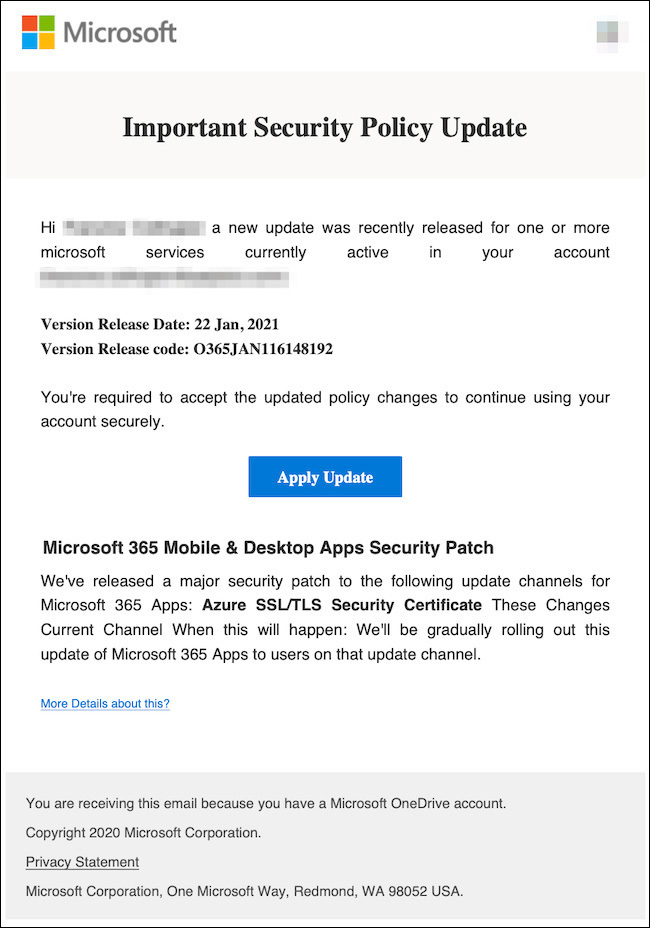
Table of Contents
The Sophistication of the Office365 Executive Inbox Attacks
The attacks weren't random; they were highly targeted and meticulously planned. Hackers employed a range of sophisticated techniques, focusing on gaining access to the accounts of high-ranking executives who often have access to sensitive financial information and decision-making power. These methods included:
-
Phishing and Spear Phishing: Hackers crafted incredibly convincing emails, often mimicking legitimate communications from trusted sources, enticing executives to click malicious links or download infected attachments. These spear-phishing attacks were highly personalized, using details gleaned from public sources to increase their effectiveness. For example, one campaign mimicked an urgent invoice from a known supplier, tailored to the specific company and the executive's role.
-
Credential Stuffing: Stolen credentials from previous data breaches were used to attempt access to Office365 accounts. This brute-force approach, coupled with social engineering tactics to obtain passwords, proved alarmingly successful.
-
Exploiting Zero-Day Vulnerabilities: In some cases, hackers exploited previously unknown vulnerabilities (zero-day exploits) in Office365 software, gaining unauthorized access before Microsoft could patch the flaws. This highlights the importance of staying up-to-date with security patches.
-
Details on how credentials were stolen: Methods included compromised passwords obtained through phishing attacks or keyloggers installed on victim's computers, allowing hackers to record keystrokes, including passwords and sensitive data.
The High Financial Stakes: Millions Lost in the Scheme
The financial ramifications of these Office365 executive inbox compromises are staggering. The attacks resulted in millions of dollars in losses for various targeted organizations. Specific examples, while often kept confidential due to reputational concerns, frequently involve:
-
Quantifiable losses: Reports indicate losses ranging from hundreds of thousands to several million dollars per compromised company. The exact figures often remain undisclosed due to legal and reputational sensitivities.
-
Wire Fraud: Hackers often intercept or redirect funds through wire transfers, exploiting the executive's authority to initiate large transactions.
-
Account Takeover: Compromised accounts allowed hackers to access and manipulate financial records, leading to fraudulent transactions.
-
Invoice Manipulation: Hackers altered invoices, inflating amounts or directing payments to fraudulent accounts.
The impact extends beyond direct financial losses. Damaged reputations, stock price fluctuations, and the cost of investigation and remediation all contribute to the substantial overall impact.
Vulnerabilities Exploited in Office365 Security
While Office365 offers a robust security infrastructure, the attacks exposed critical vulnerabilities often stemming from human error and inadequate security practices:
-
Lack of Multi-Factor Authentication (MFA): Many targeted organizations lacked MFA, a crucial security layer that adds an extra authentication step beyond passwords, significantly hindering unauthorized access.
-
Weak Password Policies: Many companies implemented insufficient password policies, using easily guessable passwords or failing to enforce regular password changes.
-
Inadequate Security Awareness Training: Employees lacked sufficient training on recognizing and avoiding phishing attempts, leaving them vulnerable to sophisticated attacks.
-
Specific Office365 Features Exploited: Attacks often exploited functionalities within Office365, such as calendar invites or shared folders, to deliver malicious content or gain access.
Protecting Your Office365 Executive Inboxes: Mitigation Strategies
Protecting against these sophisticated attacks requires a multi-layered approach:
-
Implement Multi-Factor Authentication (MFA): MFA is paramount. Enforce it for all users, especially executives.
-
Robust Password Policies: Enforce strong, unique passwords, and implement regular password rotation policies. Consider password managers for secure password storage.
-
Comprehensive Security Awareness Training: Educate employees about phishing and other social engineering tactics. Regular training sessions and simulated phishing campaigns are vital.
-
Regular Security Audits and Penetration Testing: Regularly assess your Office365 security posture and conduct penetration testing to identify and address vulnerabilities.
-
Advanced Threat Protection: Utilize Office 365's advanced threat protection tools to detect and block malicious emails and attachments.
Securing Your Office365 Executive Inboxes: A Call to Action
The multi-million dollar Office365 executive inbox hacking scheme serves as a stark reminder of the ever-evolving cyber threat landscape. The financial consequences are severe, but by proactively implementing the mitigation strategies discussed above – focusing on MFA, strong passwords, comprehensive security awareness training, and regular security audits – organizations can significantly reduce their vulnerability to these attacks. Don’t wait for an incident to occur; review your Office 365 security protocols immediately. Protecting your executive inboxes and preventing Office365 attacks is not just a matter of security; it's a matter of safeguarding your organization’s financial future and reputation. Explore additional resources on Office 365 security best practices from Microsoft and reputable cybersecurity firms to bolster your defenses. Secure your Office 365 environment today.

Featured Posts
-
 Ufc Fight Night Sandhagen Vs Figueiredo Complete Preview And Predictions
May 04, 2025
Ufc Fight Night Sandhagen Vs Figueiredo Complete Preview And Predictions
May 04, 2025 -
 Onde Assistir Ao Jogo Portuguesa X Corinthians Pelo Paulistao
May 04, 2025
Onde Assistir Ao Jogo Portuguesa X Corinthians Pelo Paulistao
May 04, 2025 -
 Tabela Do Brasileirao Serie A 2024 Datas E Horarios Confirmados Pela Cbf
May 04, 2025
Tabela Do Brasileirao Serie A 2024 Datas E Horarios Confirmados Pela Cbf
May 04, 2025 -
 Kanye West And Bianca Censori Spanish Dinner Date After Split Claims
May 04, 2025
Kanye West And Bianca Censori Spanish Dinner Date After Split Claims
May 04, 2025 -
 Review The Count Of Monte Cristo A Modern Adaptation
May 04, 2025
Review The Count Of Monte Cristo A Modern Adaptation
May 04, 2025
