Office365 Security Breach: Millions Lost As Crook Targets Executive Inboxes

Table of Contents
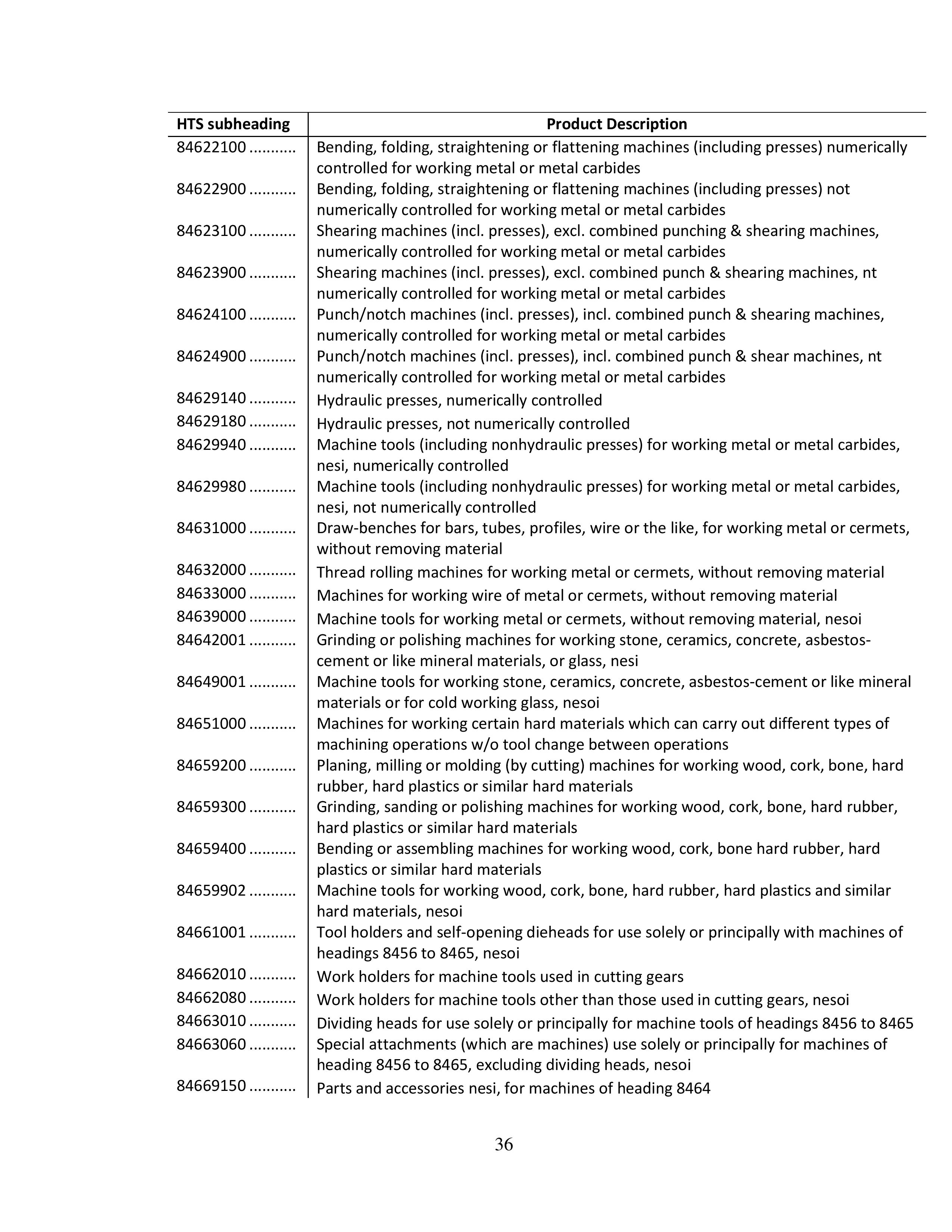
Understanding the Office365 Security Breach Vulnerability
The vulnerability exploited in this particular Office365 security breach leveraged a combination of sophisticated techniques, highlighting the multifaceted nature of modern cyberattacks. The criminals primarily targeted executive inboxes due to their access to sensitive financial information and decision-making authority. This executive inbox compromise allowed for a high degree of control and manipulation.
Common attack vectors used in Office365 breaches include:
- Sophisticated Phishing Emails: These emails often mimic legitimate communications from trusted sources, tricking recipients into revealing sensitive information or clicking malicious links. The attackers carefully crafted these emails to bypass spam filters and appear authentic.
- Malicious Attachments: Infected attachments containing malware, such as ransomware or keyloggers, are a common entry point for attackers. These attachments can compromise systems and grant access to sensitive data.
- Exploitation of Software Vulnerabilities: Attackers exploit known vulnerabilities in Office365 applications and underlying systems, often leveraging zero-day exploits for maximum impact. Keeping software up-to-date is crucial to mitigate this risk.
- Credential Stuffing Attacks: Attackers use stolen credentials obtained from other breaches to attempt access to Office365 accounts. This highlights the importance of strong, unique passwords for each account.
This data breach exposed the critical weakness in email security and overall data protection measures within the Office365 environment, stressing the need for a multi-layered approach to security.
The Impact of the Executive Inbox Compromise
The financial losses incurred due to this Office365 security breach reached into the millions, demonstrating the significant cost of a successful cyberattack. Access to executive inboxes allowed the criminals to execute wire fraud schemes, transferring funds to offshore accounts. This highlights the devastating consequences of a successful executive inbox compromise.
The consequences of this breach extend beyond mere financial loss:
- Significant Financial Losses: Millions of dollars were lost directly due to fraudulent wire transfers and other financial manipulations.
- Severe Reputational Damage: The breach significantly damaged the reputation of the affected organization, impacting customer trust and potentially leading to the loss of business.
- Legal Ramifications and Potential Fines: The organization faces significant legal ramifications, including potential regulatory fines for non-compliance with data protection regulations.
- Loss of Sensitive Data: The compromise of executive inboxes exposed confidential business information, intellectual property, and sensitive customer data.
This case underscores the broader implications for all businesses relying on Office365 for their daily operations and communication, emphasizing the need for proactive security measures.
Best Practices for Preventing Office365 Security Breaches
Protecting your organization from Office365 security breaches requires a multi-pronged approach encompassing technological solutions and employee training. Proactive security is paramount.
Preventative measures include:
- Implementing Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of authentication, significantly reducing the risk of unauthorized access.
- Regular Security Awareness Training for Employees: Educate employees about phishing scams, malicious attachments, and other common attack vectors. Regular training is crucial to reinforce good security practices.
- Strong, Unique Passwords: Enforce the use of strong, unique passwords for all Office365 accounts, and consider using a password manager to simplify this process.
- Keeping Software Updated: Regularly update all software and applications with the latest security patches to address known vulnerabilities.
- Robust Anti-Malware and Anti-Phishing Solutions: Employ robust security solutions that can detect and block malware and phishing attempts.
- Regular Security Audits and Penetration Testing: Regularly assess your Office365 security posture through security audits and penetration testing to identify and address potential vulnerabilities.
- Implementing Data Loss Prevention (DLP) Measures: Implement DLP measures to prevent sensitive data from leaving your organization's network.
- Leveraging Security Information and Event Management (SIEM) Systems: SIEM systems provide real-time monitoring and analysis of security events, enabling faster threat detection and response.
The Role of Human Error in Office365 Security Breaches
Human error plays a significant role in many Office365 security breaches. Even the most robust security systems can be circumvented by a careless click.
Common human errors include:
- Falling for Phishing Scams: Clicking on malicious links or opening infected attachments can lead to a successful breach.
- Using Weak or Easily Guessable Passwords: Weak passwords make it easy for attackers to gain access to accounts.
- Ignoring Security Warnings: Dismissing security warnings from Office365 or other applications can leave systems vulnerable.
Addressing human error requires comprehensive employee training and awareness programs that reinforce good security practices. Regular phishing simulations can effectively educate employees on recognizing and avoiding such threats.
Conclusion: Safeguarding Your Business from Office365 Security Breaches
The Office365 security breach detailed above illustrates the devastating consequences of inadequate cybersecurity measures. The financial losses, reputational damage, and legal ramifications highlight the critical need for proactive security strategies. Protecting your business from similar incidents requires a combination of technological solutions and a culture of security awareness among your employees. Implementing multi-factor authentication, regular security training, strong passwords, and robust security software are crucial steps in safeguarding your valuable data and protecting your organization. Don't become the next victim of an Office365 security breach. Implement robust security measures today to safeguard your valuable data and protect your business. For additional resources on improving your Microsoft 365 security and cloud security practices, explore [link to relevant resources, e.g., Microsoft Security documentation].

Featured Posts
-
 Us Tariffs Prompt Brookfield To Re Evaluate Manufacturing Plans
May 03, 2025
Us Tariffs Prompt Brookfield To Re Evaluate Manufacturing Plans
May 03, 2025 -
 How To Get Wwe Skins In Fortnite Cody Rhodes And The Undertaker
May 03, 2025
How To Get Wwe Skins In Fortnite Cody Rhodes And The Undertaker
May 03, 2025 -
 Report Play Station Showcase Imminent After Two Year Hiatus
May 03, 2025
Report Play Station Showcase Imminent After Two Year Hiatus
May 03, 2025 -
 Maines Groundbreaking Post Election Audit Pilot
May 03, 2025
Maines Groundbreaking Post Election Audit Pilot
May 03, 2025 -
 Netanyahu Accuse Macron De Grave Erreur Sur Le Projet D Etat Palestinien
May 03, 2025
Netanyahu Accuse Macron De Grave Erreur Sur Le Projet D Etat Palestinien
May 03, 2025
Latest Posts
-
 Barrow Afc Supporters Pedal For Charity In Sky Bet Relay
May 03, 2025
Barrow Afc Supporters Pedal For Charity In Sky Bet Relay
May 03, 2025 -
 Alkrh Aljmahyry 30 Shkhsyt Mthyrt Lljdl Fy Ealm Krt Alqdm Mwqe Bkra
May 03, 2025
Alkrh Aljmahyry 30 Shkhsyt Mthyrt Lljdl Fy Ealm Krt Alqdm Mwqe Bkra
May 03, 2025 -
 Mwqe Bkra Akthr 30 Ryadya Mkrwhyn Fy Ealm Krt Alqdm
May 03, 2025
Mwqe Bkra Akthr 30 Ryadya Mkrwhyn Fy Ealm Krt Alqdm
May 03, 2025 -
 The Internal Fight Within Reform Uk Impact And Analysis
May 03, 2025
The Internal Fight Within Reform Uk Impact And Analysis
May 03, 2025 -
 Aedae Aljmahyr Akthr 30 Shkhsyt Ghyr Mhbwbt Fy Tarykh Krt Alqdm Mwqe Bkra
May 03, 2025
Aedae Aljmahyr Akthr 30 Shkhsyt Ghyr Mhbwbt Fy Tarykh Krt Alqdm Mwqe Bkra
May 03, 2025
