Millions In Losses After Widespread Office365 Executive Account Compromise
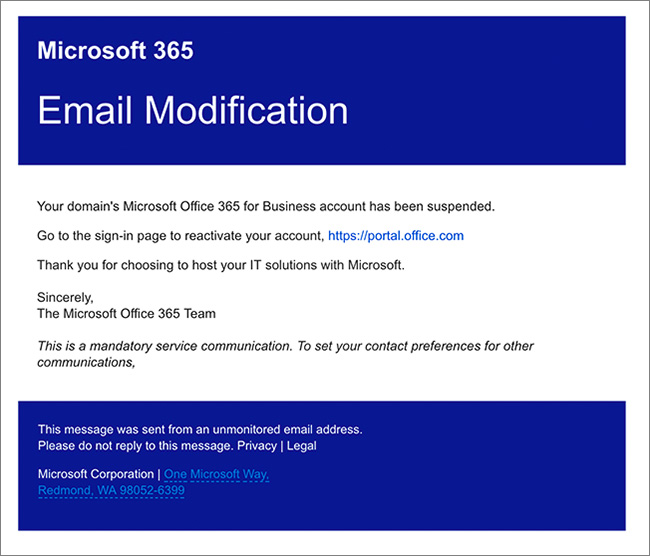
Table of Contents
The Methods Behind Office365 Executive Account Compromises
Cybercriminals employ various tactics to gain unauthorized access to high-value Office365 executive accounts. Understanding these methods is the first step towards effective prevention.
Phishing and Spear Phishing Attacks
Phishing remains a highly effective weapon in the attacker's arsenal. Spear phishing, a more targeted approach, is particularly dangerous, as it leverages personalized information to increase the likelihood of success.
- Example email subject lines: "Urgent: Contract Review Required," "Financial Report Attached," "Important Security Update."
- Attachment types: Malicious .doc, .xls, .pdf files containing malware or links to compromised websites.
- Social engineering techniques: Creating a sense of urgency, exploiting trust relationships, mimicking legitimate communication styles.
- MFA Bypass: Attackers often try to bypass multi-factor authentication (MFA) through techniques like SIM swapping or phishing for one-time codes.
Credential Stuffing and Brute-Force Attacks
Attackers frequently employ credential stuffing, using stolen credentials from data breaches on other platforms to attempt logins on Office365. Brute-force attacks involve systematically trying numerous password combinations.
- Password Managers: Weak passwords stored in insecure password managers are prime targets.
- Password Reuse: Reusing the same password across multiple platforms significantly increases the risk of compromise.
- Stolen Databases: Leaked databases containing usernames and passwords from various websites fuel these attacks.
Exploiting Vulnerabilities in Third-Party Apps
Many organizations integrate third-party apps into their Office365 environment. Vulnerabilities in these apps can provide a backdoor for attackers.
- Vulnerable Apps: Outdated or poorly secured apps represent significant security risks.
- App Vetting: Thorough vetting of third-party apps before integration is crucial.
- Security Updates: Regular updates for all apps are essential to patch known vulnerabilities.
- Shadow IT: The use of unsanctioned apps ("shadow IT") poses a major threat and often goes undetected.
The Devastating Consequences of an Office365 Executive Account Compromise
The repercussions of a successful Office365 executive account compromise can be catastrophic, impacting both the bottom line and the organization's reputation.
Financial Losses
The financial consequences can be staggering.
- Ransomware Demands: Attackers may encrypt critical data and demand a ransom for its release.
- Wire Transfer Fraud: Compromised accounts can be used to initiate fraudulent wire transfers.
- Intellectual Property Theft: Confidential company information, including trade secrets and intellectual property, can be stolen.
- Average Breach Costs: The average cost of a data breach can run into millions of dollars.
Reputational Damage
A security breach can severely damage an organization's reputation.
- Loss of Customer Trust: Customers may lose confidence in the organization's ability to protect their data.
- Negative Publicity: Public disclosure of a breach can lead to negative media coverage and damage to brand image.
- Impact on Investor Confidence: Investors may lose confidence, impacting stock prices and future investments.
Data Breaches and Regulatory Penalties
Data breaches can trigger significant legal and regulatory ramifications.
- GDPR and CCPA Compliance: Non-compliance with regulations like GDPR and CCPA can result in substantial fines.
- Regulatory Penalties: Government agencies may impose significant penalties for failing to protect sensitive data.
- Data Privacy: Strong data privacy and security protocols are essential to mitigate these risks.
Protecting Your Organization from Office365 Executive Account Compromises
Proactive security measures are essential to prevent Office365 executive account compromises.
Implementing Strong Authentication Measures
Robust authentication is the first line of defense.
- Multi-Factor Authentication (MFA): Implement MFA for all accounts, including executive accounts.
- Password Managers: Utilize secure password managers to generate and store strong, unique passwords.
- Password Policies: Enforce strong password policies, including complexity requirements and regular password changes.
Security Awareness Training
Educating employees is critical to preventing phishing attacks.
- Security Awareness Training Programs: Implement regular, engaging security awareness training programs.
- Phishing Simulations: Conduct regular phishing simulations to test employee awareness and response.
- Ongoing Reinforcement: Continuously reinforce security best practices through regular updates and reminders.
Regular Security Audits and Penetration Testing
Proactive security measures are crucial.
- Vulnerability Assessments: Regularly conduct vulnerability assessments to identify and address security weaknesses.
- Penetration Testing: Simulate real-world attacks to test the organization's security posture.
- Audit Frequency: Regular security audits and penetration testing should be conducted at least annually, ideally more frequently.
Conclusion
The threat of Office365 executive account compromise is real and demands immediate attention. Understanding the methods used by attackers, the potential consequences, and the necessary preventative measures is paramount. By implementing strong authentication, comprehensive security awareness training, and regular security audits, organizations can significantly reduce their risk. Don't wait until it's too late. Proactively strengthen your Office 365 security and protect your organization from the devastating impact of an executive account security breach. Contact us today for a free security assessment and let us help you safeguard your business.

Featured Posts
-
 Freeway Series Mookie Betts Out Due To Ongoing Health Issue
May 08, 2025
Freeway Series Mookie Betts Out Due To Ongoing Health Issue
May 08, 2025 -
 Post Roe America How Otc Birth Control Reshapes Family Planning
May 08, 2025
Post Roe America How Otc Birth Control Reshapes Family Planning
May 08, 2025 -
 Will Trumps Next Speech Send Bitcoin Soaring Above 100 000 A Price Prediction Analysis
May 08, 2025
Will Trumps Next Speech Send Bitcoin Soaring Above 100 000 A Price Prediction Analysis
May 08, 2025 -
 Sony Ps 5 Pro A Deep Dive Into Its Liquid Metal Cooling System Via Official Teardown
May 08, 2025
Sony Ps 5 Pro A Deep Dive Into Its Liquid Metal Cooling System Via Official Teardown
May 08, 2025 -
 Oklahoma City Thunder Vs Houston Rockets Where To Watch Betting Predictions And Game Analysis
May 08, 2025
Oklahoma City Thunder Vs Houston Rockets Where To Watch Betting Predictions And Game Analysis
May 08, 2025
Latest Posts
-
 The Thunder Vs The National Media A Heated Confrontation
May 08, 2025
The Thunder Vs The National Media A Heated Confrontation
May 08, 2025 -
 The Long Walk Trailer A Stephen King Approved Dark Thriller
May 08, 2025
The Long Walk Trailer A Stephen King Approved Dark Thriller
May 08, 2025 -
 First Trailer Hunger Games Directors New Dystopian Horror Film Based On Stephen King
May 08, 2025
First Trailer Hunger Games Directors New Dystopian Horror Film Based On Stephen King
May 08, 2025 -
 Dispute Erupts Between Okc Thunder And National Media
May 08, 2025
Dispute Erupts Between Okc Thunder And National Media
May 08, 2025 -
 Dystopian Horror Movie Based On Stephen King Novel First Trailer Drops
May 08, 2025
Dystopian Horror Movie Based On Stephen King Novel First Trailer Drops
May 08, 2025
