Millions In Losses: Office365 Executive Account Hack Exposes Security Gaps

Table of Contents
The Tactics Used in Office365 Executive Account Hacks
Cybercriminals employ sophisticated techniques to gain access to executive Office365 accounts. Understanding these tactics is crucial for effective prevention.
Phishing and Spear Phishing Attacks
Sophisticated phishing and spear-phishing emails are the most common entry point for attackers. These emails leverage social engineering techniques, using personalized lures and mimicking legitimate communications to trick unsuspecting executives into revealing sensitive information or clicking malicious links.
- Personalized Lures: Attackers often research their targets, tailoring emails to include details about their work, projects, or personal interests to increase credibility.
- Malicious Links and Attachments: Emails may contain links leading to fake login pages designed to steal credentials or attachments carrying malware.
- Real-World Examples: A recent attack involved a convincing email seemingly from the CEO requesting urgent financial transfer details. Another example involved a fake invoice attachment containing ransomware.
- Keywords: phishing, spear phishing, social engineering, email security, Office365 phishing protection
Credential Stuffing and Brute-Force Attacks
Stolen credentials from other breaches are frequently used in credential stuffing attacks. Attackers systematically try these credentials against Office365 accounts. Weak passwords are particularly vulnerable to brute-force attacks, where software tries numerous password combinations until a match is found.
- Data Breaches as a Source: The dark web is a rich source of stolen credentials from various websites and services.
- Weak Passwords: Using easily guessable passwords or reusing the same password across multiple accounts significantly increases the risk.
- MFA as a Defense: Multi-factor authentication (MFA) adds a significant layer of security, making it much harder for attackers to gain access even with stolen credentials.
- Keywords: credential stuffing, brute-force attack, password security, multi-factor authentication, MFA, Office365 password protection
Exploiting Third-Party Applications and Integrations
Many organizations integrate third-party applications with Office365 to enhance productivity. However, poorly secured apps can introduce significant vulnerabilities. Attackers might exploit weaknesses in these apps to gain unauthorized access to Office365 accounts.
- Vetting Third-Party Apps: Thoroughly vetting all third-party applications before integration is crucial to minimize risks.
- Regular Security Audits: Regularly auditing the security posture of integrated applications is essential to identify and address potential vulnerabilities.
- API Security: Secure APIs and proper authorization mechanisms are critical to protect against unauthorized access through integrated applications.
- Keywords: third-party application security, API security, Office365 app security, integration risks
The Consequences of a Successful Office365 Executive Account Breach
A successful breach of an executive Office365 account can have severe and far-reaching consequences.
Financial Losses and Reputational Damage
Data theft, ransomware attacks, and business disruption can lead to substantial financial losses. The reputational damage resulting from a data breach can be equally devastating, eroding customer trust and impacting brand value.
- Ransomware Attacks: Attackers might encrypt sensitive data and demand a ransom for its release.
- Data Theft: Confidential information, including financial data, intellectual property, and customer data, might be stolen and sold on the dark web.
- Loss of Customer Trust: A data breach can severely damage an organization's reputation, leading to a loss of customers and business opportunities.
- Keywords: data loss, ransomware, reputational damage, brand impact, financial crime
Legal and Regulatory Compliance Issues
Data breaches trigger legal and regulatory compliance issues, particularly concerning GDPR and other data privacy regulations. Organizations face hefty fines and potential legal action for failing to protect sensitive data.
- GDPR Compliance: Non-compliance with GDPR can result in substantial fines, reaching millions of euros.
- Data Breach Notification: Organizations are legally obligated to notify affected individuals and authorities about data breaches within specified timeframes.
- Legal Action: Affected individuals and organizations may initiate legal action against the breached company.
- Keywords: GDPR, data privacy, legal compliance, regulatory fines, data breach notification
Operational Disruption and Loss of Productivity
A compromised account can significantly disrupt business operations, leading to lost productivity. Remediation and recovery efforts consume valuable time and resources.
- Business Interruption: Access to critical systems and data may be disrupted, hindering business operations.
- Recovery Time: Restoring systems and data after a breach can take days or even weeks.
- Incident Response Costs: The costs associated with incident response, including investigation, remediation, and legal fees, can be substantial.
- Keywords: business disruption, productivity loss, recovery time, incident response
Conclusion: Strengthening Your Office365 Security Posture and Preventing Executive Account Hacks
The vulnerabilities highlighted—phishing attacks, weak passwords, and insecure third-party applications—underscore the critical need for robust Office365 security. The significant financial and reputational consequences of an Office365 executive account breach cannot be overstated.
To mitigate these risks, implement the following recommendations:
- Implement strong multi-factor authentication (MFA).
- Regularly train employees on phishing awareness and cybersecurity best practices.
- Carefully vet and monitor third-party applications integrated with Office365.
- Conduct regular security audits and penetration testing.
Protect your organization from the devastating consequences of an Office365 executive account hack by implementing robust security measures today. Strengthen your Office365 security and prevent costly executive account compromises. Don't wait until it's too late—secure your Office365 environment now.

Featured Posts
-
 Post Night Out Annie Kilner Seen Without Wedding Ring
May 24, 2025
Post Night Out Annie Kilner Seen Without Wedding Ring
May 24, 2025 -
 U S Tariff Delay Triggers 8 Stock Market Rise On Euronext Amsterdam
May 24, 2025
U S Tariff Delay Triggers 8 Stock Market Rise On Euronext Amsterdam
May 24, 2025 -
 Los Angeles Wildfires Fuel A Disturbing New Gambling Market
May 24, 2025
Los Angeles Wildfires Fuel A Disturbing New Gambling Market
May 24, 2025 -
 Canadian Auto Execs Demand Stronger Action Against Trumps Threats
May 24, 2025
Canadian Auto Execs Demand Stronger Action Against Trumps Threats
May 24, 2025 -
 Sean Penn Weighs In On Dylan Farrows Accusations Against Woody Allen
May 24, 2025
Sean Penn Weighs In On Dylan Farrows Accusations Against Woody Allen
May 24, 2025
Latest Posts
-
 New York City Memorial Day Weekend Weather Prediction And Rain Outlook
May 24, 2025
New York City Memorial Day Weekend Weather Prediction And Rain Outlook
May 24, 2025 -
 Stitchpossibles Weekend Success A Look At The Potential For A Historic 2025 Box Office
May 24, 2025
Stitchpossibles Weekend Success A Look At The Potential For A Historic 2025 Box Office
May 24, 2025 -
 Best Memorial Day 2025 Sales Laptops Beauty And More
May 24, 2025
Best Memorial Day 2025 Sales Laptops Beauty And More
May 24, 2025 -
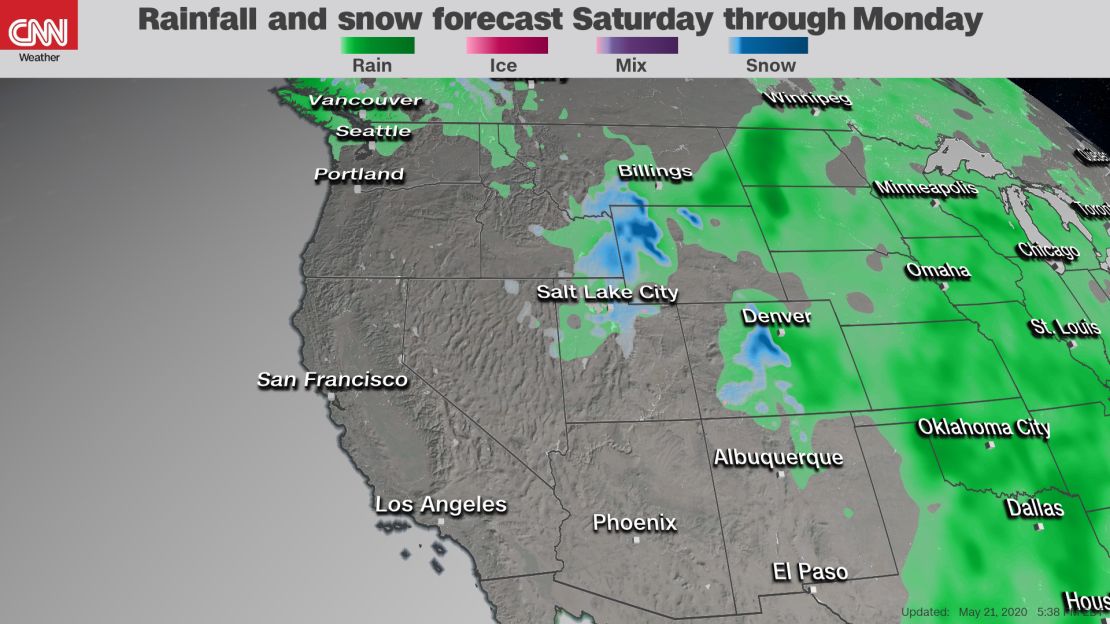 Memorial Day Weekend Rain Forecast For New York City
May 24, 2025
Memorial Day Weekend Rain Forecast For New York City
May 24, 2025 -
 Box Office Battle Brewing Stitchpossible Weekend And The Potential For 2025 Records
May 24, 2025
Box Office Battle Brewing Stitchpossible Weekend And The Potential For 2025 Records
May 24, 2025
