Millions Stolen: Insider Threat Or Sophisticated Office365 Hack?

Table of Contents
The Rising Threat of Office365 Breaches
Office 365, while offering incredible productivity benefits, has become a prime target for cybercriminals. Its ubiquitous nature and the wealth of sensitive data it holds make it a lucrative prize for both internal and external attackers. The increasing reliance on cloud-based services, coupled with the ever-evolving sophistication of hacking techniques, creates a potent cocktail of risk. Many organizations, unfortunately, still lack robust security measures, exacerbating the problem.
- Increased reliance on cloud-based services: The shift to cloud computing means more data resides outside traditional network perimeters, creating new attack surfaces.
- Sophistication of hacking techniques: Cybercriminals constantly refine their methods, employing advanced techniques like phishing, credential stuffing, and exploiting zero-day vulnerabilities.
- Lack of robust security measures: Many organizations fail to implement crucial security measures, such as multi-factor authentication (MFA) and regular security awareness training, leaving their Office365 environments vulnerable.
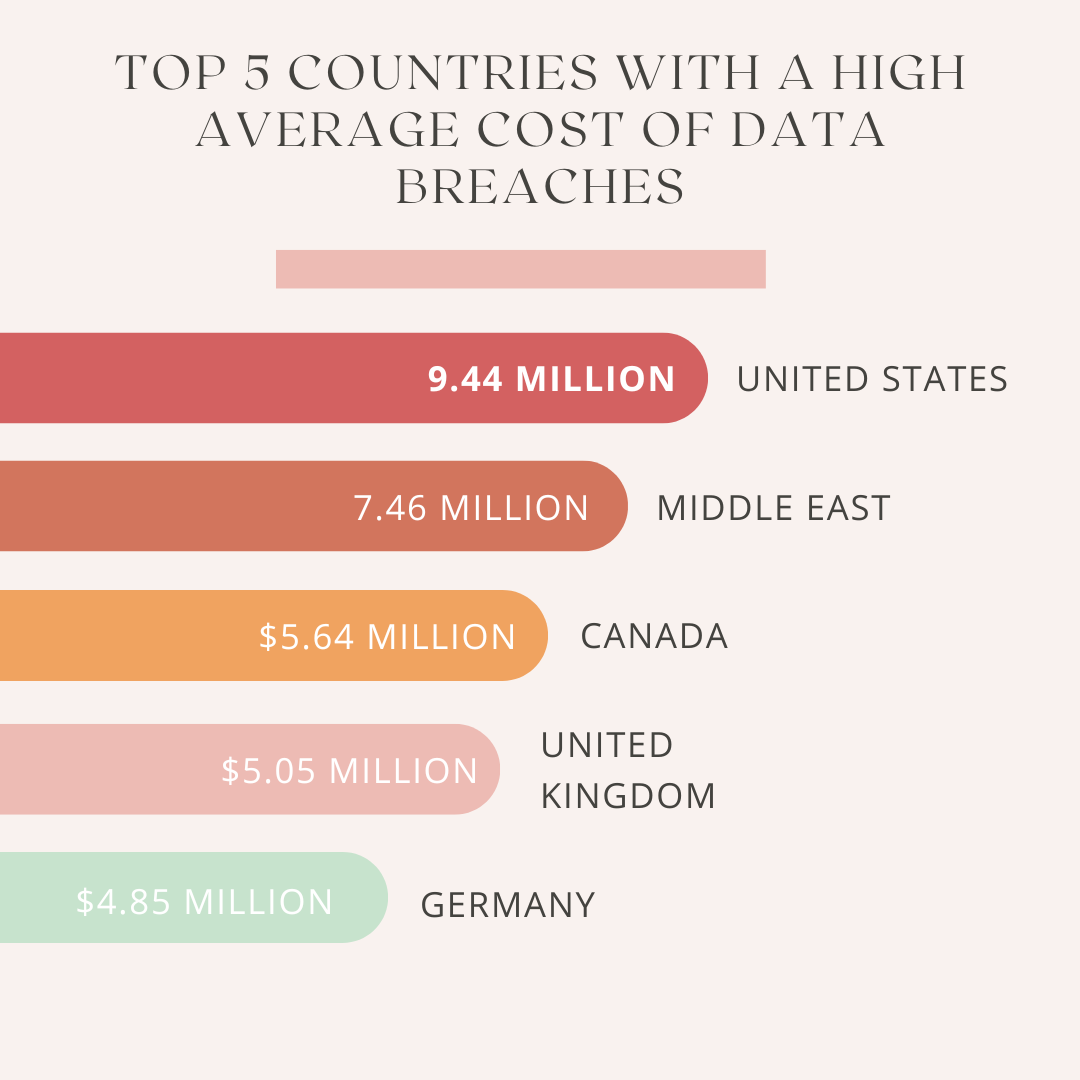
Recent studies indicate a staggering increase in Office 365 breaches, resulting in significant financial losses for businesses of all sizes. The average cost of a data breach continues to rise, impacting not only financial stability but also brand reputation and customer trust.
Identifying the Culprit: Insider Threat vs. External Attack
Distinguishing between an insider threat and a sophisticated external attack can be incredibly challenging. Both can employ similar techniques, resulting in overlapping indicators and making attribution difficult.
Insider Threats: These involve malicious or negligent actions by individuals within the organization. Motives can range from financial gain to revenge or simple carelessness. Identifying insider threats often relies on behavioral analysis and detecting anomalies.
- Insider threat indicators: Unusual access patterns outside normal working hours, suspicious data exfiltration attempts, unauthorized access to sensitive files.
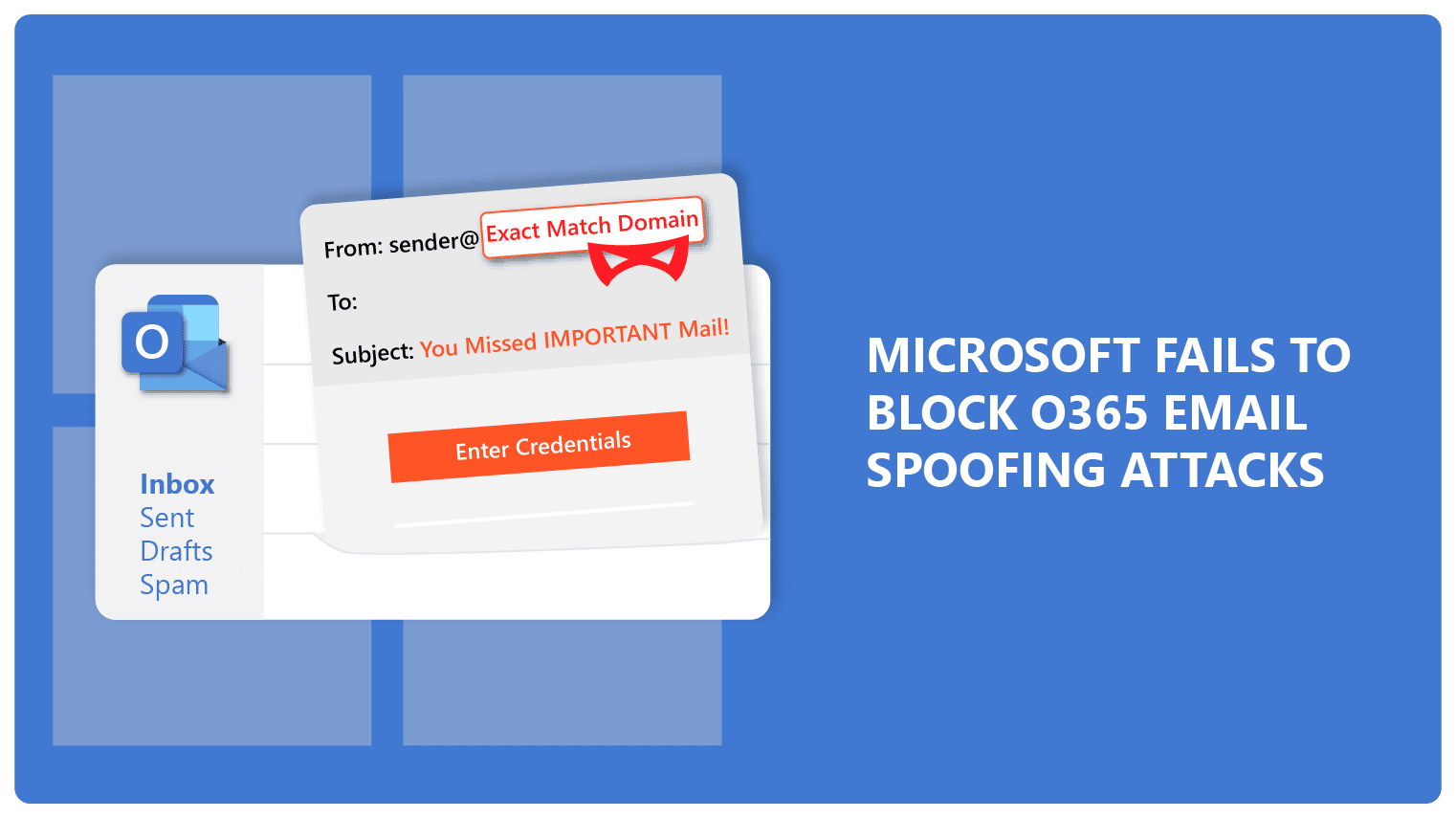
External Attacks: These originate from outside the organization and often leverage techniques such as phishing campaigns, credential stuffing, and exploiting known vulnerabilities in Office 365 applications or infrastructure.
- External attack indicators: Widespread phishing emails targeting multiple users, compromised credentials appearing on the dark web, malware infections within the network.
Overlapping Indicators: The lines blur when considering that compromised accounts, whether through phishing or insider collusion, can lead to similar data loss patterns. The challenge lies in determining the root cause of the compromise.
Analyzing the "Millions Stolen" Scenario: A Case Study Approach
Let's consider a hypothetical scenario: a company experiences a significant Office365 breach, resulting in the theft of millions of dollars worth of sensitive data.
Insider Threat Perspective: A disgruntled employee with access to financial systems might have exfiltrated data, potentially motivated by revenge or financial gain.
- Potential motives: Retaliation for perceived unfair treatment, financial hardship, or seeking employment elsewhere.
External Attack Perspective: A sophisticated phishing campaign could have compromised multiple user credentials, granting attackers access to sensitive information.
- Sophisticated techniques: Highly targeted spear-phishing emails, use of advanced persistent threats (APTs) to maintain long-term access.
Forensic Investigation: Determining the source requires a thorough forensic investigation. This involves analyzing system logs, network traffic, and user activity to identify patterns and anomalies that might point to the source of the breach.
- Forensic investigation techniques: Log analysis, network forensics, malware analysis, user behavior analysis.
Strengthening Office365 Security: Prevention and Mitigation Strategies
Proactive security measures are crucial to prevent Office365 hacks. A multi-layered approach combining technical controls, employee training, and regular assessments is essential.
- Implement MFA for all accounts: This adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain usernames and passwords.
- Regular security awareness training for employees: Educate employees about phishing scams, social engineering tactics, and safe password practices.
- Utilize advanced threat protection features in Office 365: Leverage built-in security features such as anti-malware, anti-phishing, and data loss prevention (DLP) capabilities.
- Enforce strong password policies: Require complex, unique passwords and encourage the use of password managers.
- Regularly back up critical data: Regular backups ensure data can be restored in case of a breach, minimizing data loss.
- Regular security audits and vulnerability assessments: Identify and address security weaknesses before they can be exploited.
Conclusion: Protecting Your Organization from Office365 Hacks
The threat of Office365 hacks, stemming from both insider threats and sophisticated external attacks, is real and significant. The financial and reputational damage resulting from a breach can be catastrophic. A comprehensive security strategy, incorporating technical controls, employee training, and proactive monitoring, is no longer optional; it's a necessity. Don't become another statistic in the "millions stolen" category. Proactively assess your Office365 security posture today. Consider engaging a cybersecurity professional for a comprehensive security assessment and implementation of robust preventative measures to safeguard your organization against Office365 hacks and other cyber threats. Your peace of mind, and your bottom line, depend on it.

Featured Posts
-
 Stockholm Stadshotell Fullstaendig Recension Fran Krogkommissionen
Apr 26, 2025
Stockholm Stadshotell Fullstaendig Recension Fran Krogkommissionen
Apr 26, 2025 -
 Planning Your April A Look Ahead At Indie Bookstore Day Kings Day And Tumbleweeds Film Fest
Apr 26, 2025
Planning Your April A Look Ahead At Indie Bookstore Day Kings Day And Tumbleweeds Film Fest
Apr 26, 2025 -
 Trumps Legacy A Herculean Task For The Next Federal Reserve Chair
Apr 26, 2025
Trumps Legacy A Herculean Task For The Next Federal Reserve Chair
Apr 26, 2025 -
 Trumps Unexpected Influence How Hes Shaping The Canadian Election
Apr 26, 2025
Trumps Unexpected Influence How Hes Shaping The Canadian Election
Apr 26, 2025 -
 Shedeur Sanders The Perfect Fit For The New York Giants
Apr 26, 2025
Shedeur Sanders The Perfect Fit For The New York Giants
Apr 26, 2025
Latest Posts
-
 Fbi Investigation Major Office365 Data Breach Results In Significant Financial Losses
Apr 27, 2025
Fbi Investigation Major Office365 Data Breach Results In Significant Financial Losses
Apr 27, 2025 -
 Millions Stolen Inside The Office365 Executive Email Hacking Scheme
Apr 27, 2025
Millions Stolen Inside The Office365 Executive Email Hacking Scheme
Apr 27, 2025 -
 Office365 Executive Email Compromise Nets Millions For Hacker Say Federal Authorities
Apr 27, 2025
Office365 Executive Email Compromise Nets Millions For Hacker Say Federal Authorities
Apr 27, 2025 -
 Exec Office365 Breach Millions Made Through Email Hacks Fbi Reveals
Apr 27, 2025
Exec Office365 Breach Millions Made Through Email Hacks Fbi Reveals
Apr 27, 2025 -
 Ohio Derailment Aftermath Persistent Toxic Chemicals In Local Buildings
Apr 27, 2025
Ohio Derailment Aftermath Persistent Toxic Chemicals In Local Buildings
Apr 27, 2025
