Office365 Data Breach Leads To Multi-Million Dollar Theft: FBI Investigation

Table of Contents
Details of the Office365 Data Breach
While the specific organization targeted in this multi-million dollar theft remains undisclosed for legal reasons, we can describe it as a large, multinational corporation in the financial services sector. The scale of their operations and the sensitivity of their data made them a particularly lucrative target for cybercriminals.
The Breach Methodology
The hackers employed a multi-stage attack leveraging several common techniques to gain access to the organization's Office365 environment. Their methodology included:
- Phishing emails targeting employees: Sophisticated phishing emails, designed to mimic legitimate communications, were sent to employees. These emails contained malicious links or attachments.
- Exploitation of weak passwords: The attackers likely used a combination of credential stuffing (trying known username/password combinations from previous data breaches) and brute-force attacks (trying numerous password variations) to compromise employee accounts.
- Compromised user accounts gaining access to sensitive data: Once access was gained, the attackers moved laterally within the network, exploiting the compromised accounts to access sensitive financial data and customer information.
Data Compromised
The data breach resulted in the theft of thousands of customer records, including personally identifiable information (PII), financial records, and sensitive internal documents. The sheer volume of data compromised significantly amplified the financial and reputational damage to the victim organization.
The Multi-Million Dollar Theft
The financial impact of this Office365 data breach is staggering. Millions of dollars were stolen through a series of carefully orchestrated fraudulent transactions.
Financial Impact
The exact amount remains under investigation, but sources close to the investigation suggest the theft exceeded several million dollars. Beyond the direct financial loss, the organization faces significant reputational damage, potential legal repercussions, and the considerable cost of remediation and enhanced security measures.
Methods of Theft
The hackers cleverly utilized the stolen data to facilitate the theft through:
- Transfer of funds to offshore accounts: Stolen financial credentials were used to initiate wire transfers to accounts located in jurisdictions known for their opacity and lack of financial oversight.
- Fake invoices and payment requests: The attackers created fraudulent invoices that mimicked legitimate business transactions, tricking the organization into transferring funds to their controlled accounts.
- Identity theft related to stolen customer data: The stolen customer data was likely used for identity theft and other fraudulent activities, resulting in further financial losses for both the organization and its customers.
The Aftermath
The immediate aftermath involved a frantic scramble to contain the damage, including freezing accounts, notifying affected customers, and engaging forensic experts to investigate the full extent of the breach. The incident led to a significant disruption of business operations and a severe blow to the organization's reputation.
The FBI Investigation
The FBI is actively investigating this significant Office365 data breach, leveraging its considerable resources and expertise.
FBI Involvement
The FBI's involvement includes tracing the stolen funds, identifying the perpetrators, and collaborating with international law enforcement agencies. This is a complex investigation requiring advanced digital forensics and international cooperation.
Investigative Techniques
The investigation likely employs various techniques, including:
- Digital forensics: Analyzing the compromised systems and data to identify the attackers’ methods and trace their activities.
- Tracing financial transactions: Following the trail of stolen funds through various financial institutions and jurisdictions.
- International cooperation: Collaborating with law enforcement agencies in other countries to track down the perpetrators who may be operating outside US borders.
Current Status
The investigation is ongoing, and further updates will be provided as they become available. While arrests haven't been publicly announced, the FBI is actively pursuing leads and working to bring those responsible to justice.
Lessons Learned and Prevention Strategies
This Office365 data breach highlights several critical weaknesses in the organization's security posture. Critically, it underscores the importance of proactive security measures to prevent similar incidents.
Weaknesses Exploited
The breach exposed vulnerabilities in password management, phishing resistance, and potentially insufficient monitoring of user activities within the Office365 environment.
Best Practices for Office365 Security
To prevent future Office365 data breaches, organizations should implement the following best practices:
- Multi-factor authentication (MFA): Mandate MFA for all users to add an extra layer of security beyond passwords.
- Regular security awareness training for employees: Educate employees about phishing scams, social engineering tactics, and password hygiene.
- Strong password policies: Enforce strong, unique passwords and encourage the use of password managers.
- Regular software updates and patching: Keep all software, including Office365 applications and underlying infrastructure, up-to-date with security patches.
- Implementing robust access control measures: Employ the principle of least privilege, granting users only the access they need to perform their jobs.
- Regular data backups and recovery plans: Ensure that regular backups of critical data are performed and that robust recovery plans are in place.
- Using advanced threat protection features in Office365: Leverage Office365's built-in security features, including advanced threat protection and data loss prevention (DLP).
Conclusion
This multi-million dollar Office365 data breach serves as a stark reminder of the ever-present threat of cyberattacks. The scale of the financial losses, the FBI’s involvement, and the lessons learned highlight the critical need for robust cybersecurity strategies. Protecting your organization from an Office365 data breach requires a multifaceted approach encompassing employee training, strong password policies, multi-factor authentication, and the implementation of advanced threat protection features. Don't wait for a similar disaster to strike; protect your organization's valuable data and reputation by implementing robust security measures today! Learn more about securing your Office365 environment and preventing costly data breaches.

Featured Posts
-
 Marvels Quality Control Are The Movies And Shows Still Good Enough
May 05, 2025
Marvels Quality Control Are The Movies And Shows Still Good Enough
May 05, 2025 -
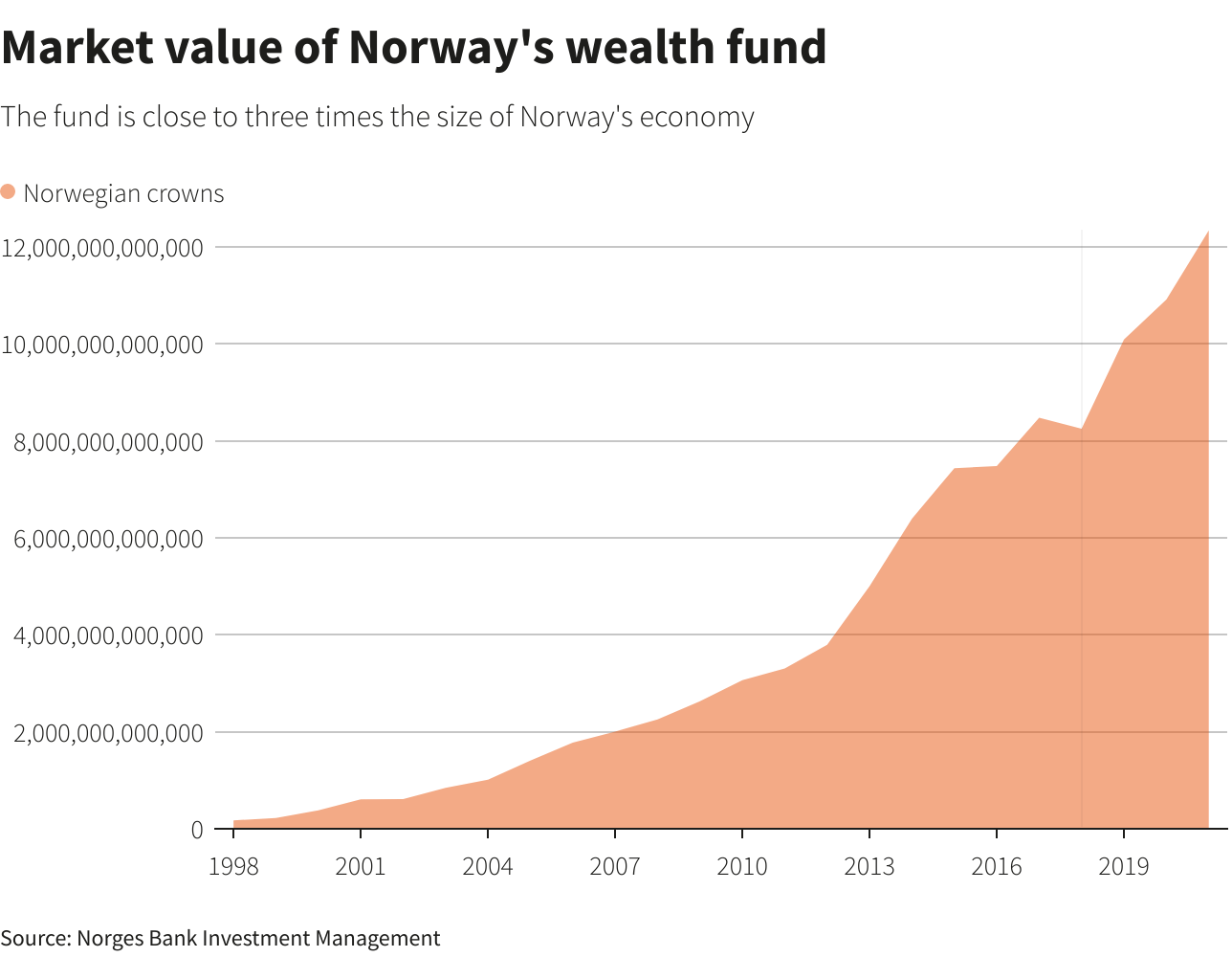 Norways Sovereign Wealth Fund And The Trump Tariff Challenge
May 05, 2025
Norways Sovereign Wealth Fund And The Trump Tariff Challenge
May 05, 2025 -
 Migrants Desperate Escape Eight Hours Hiding In A Tree From Ice
May 05, 2025
Migrants Desperate Escape Eight Hours Hiding In A Tree From Ice
May 05, 2025 -
 Triangle Shaped Jet From Jet Zero Projected Launch By Late 2027
May 05, 2025
Triangle Shaped Jet From Jet Zero Projected Launch By Late 2027
May 05, 2025 -
 Fox 2 To Simulcast Select Red Wings And Tigers Games
May 05, 2025
Fox 2 To Simulcast Select Red Wings And Tigers Games
May 05, 2025
Latest Posts
-
 Emma Stooyn Vs Margkaret Koyalei Ti Pragmatika Synevi Sta Oskar
May 05, 2025
Emma Stooyn Vs Margkaret Koyalei Ti Pragmatika Synevi Sta Oskar
May 05, 2025 -
 Oskar 2024 Diavasame Ta Xeili Tis Emma Stooyn Kai Tis Margkaret Koyalei
May 05, 2025
Oskar 2024 Diavasame Ta Xeili Tis Emma Stooyn Kai Tis Margkaret Koyalei
May 05, 2025 -
 Emma Stooyn Kai Margkaret Koyalei Symvan Sta Oskar Analysi Vinteo
May 05, 2025
Emma Stooyn Kai Margkaret Koyalei Symvan Sta Oskar Analysi Vinteo
May 05, 2025 -
 Emma Stoun U Minispidnitsi Foto Z Premiyi Shou Biznes
May 05, 2025
Emma Stoun U Minispidnitsi Foto Z Premiyi Shou Biznes
May 05, 2025 -
 Emma Stones Dress At Snls 50th Anniversary A Style Statement
May 05, 2025
Emma Stones Dress At Snls 50th Anniversary A Style Statement
May 05, 2025
